Thousands of taxpayers’ personal details potentially exposed online through councils’ debt-chasing texts
Exclusive Bulk SMS messages sent by local councils across the UK contained weblinks leading to pages that freely exposed to the public thousands of taxpayers’ names, addresses, and outstanding debts, The Register can reveal.
Text messages sent by Telsolutions Ltd on behalf of a dozen local authorities contained shortlinks to webpages urging council tax defaulters to pay up – and in a dozen cases seen by The Register there was little or no authentication protecting personal data from prying eyes.
Sent in bulk by around a dozen councils, the messages have reached thousands of defaulters and late payers, although the loophole allowing the data leak has since been closed.
Government statistics [PDF, 16 pages, table 2] show that in England around 3 per cent of council taxes by value were not collected during financial year 2019/20.
Faced with defaulters, councils have turned to text messages for chasing those who haven’t paid on time. As Barnet Council put it: “The Council Tax Service will send SMS text messages, emails and recorded voice messages to you if your Council Tax account falls in to arrears.”
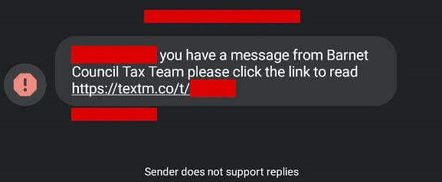
As part of that service, many councils around the UK use contractors to send those messages. One of those contractors is Telsolutions – and Register reader Jim was very concerned when his council sent him a message with a link in the format textm[.]co/abcde.
Following the link yielded a web page showing his personal data with minimal security – and our reader realised that changing the alphanumeric characters in the URL showed him copies of other people’s data. Including, as he told us, information about people who lived in completely separate council areas.
Upon investigating the enumerable URLs, it was discovered that London’s Bexley Council, a user of the Telsolutions service, had implemented no authentication at all. Anyone could freely view the full details of an alleged tax defaulter in the borough without proving their identity.
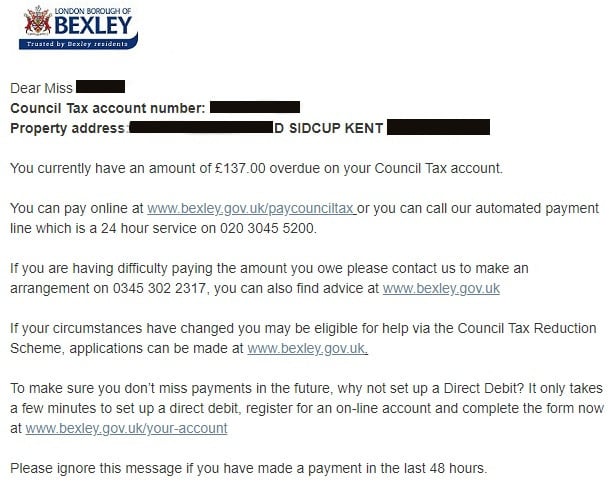
Bexley Council potentially exposed all of its council taxpayers’ details via an SMS service with no authentication at all
To view the information of another taxpayer, all the recipient needed to do was follow the URL from the SMS, alter the alphanumeric characters, and click a button labelled “proceed”.
Some councils, such as Walsall in Birmingham, also used disclaimer text with a “proceed” button underneath.
Such click-through “security” protecting personal data from public exposure is meaningless.
Other councils used the Telsolutions system in similar ways. For example, Southampton City Council showed a person’s full name and asked for a postcode as verification to view further data.
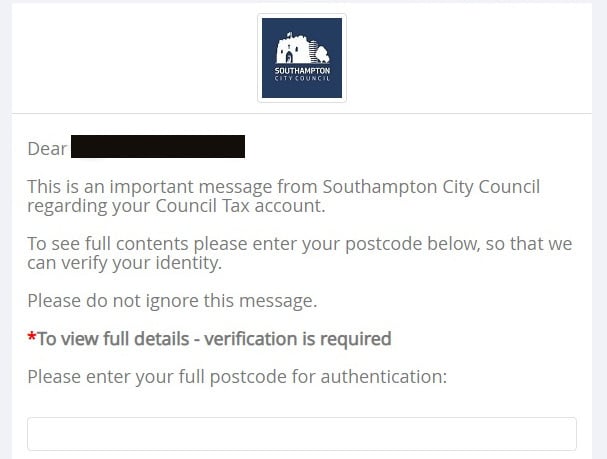
Southampton City Council was a user of this SMS service, using easily found postcodes for ‘authentication’
The Register pointed out to seven councils using this postcode-based “authentication” system that, for example, using a search engine to look up “Joe Bloggs Southampton” invariably returned address suggestions (complete with postcodes) from sites such as Yell in the top results. A mildly determined criminal could easily use an electoral register lookup service to get a confirmed match.
We counted 14 councils using the system, of which just under a dozen were exposing personal data with few or no meaningful controls. These councils were: Barnet; Bexley; Brighton; Cardiff; Coventry City; Greenwich; Lambeth; Redbridge; Southampton City; and Walsall. Between them, these local authority areas are responsible for more than three million council taxpayers.
Other councils also used the same system, but Telsolutions shortlinks showing their logos returned error strings in place of taxpayers’ names and addresses, suggesting that the councils may have ceased using the system.
The common denominator: loophole closed
Telsolutions advertises itself under the slogan “your proactive customer communications partner”. Its website also boasts of its status as an approved government G-Cloud supplier and of being on the Crown Commercial Services framework – as well as holding Cyber Essentials certification.
Chief exec Rob Perry-Jones told us: “We take security and all matters of data protection extremely seriously. After identifying a potential vulnerability with one of our systems, we suspended the service immediately and have since further increased security and introduced new measures to prevent malicious intent. Those clients potentially affected have been notified and the service adjusted with new measures.”
ESET cyber security specialist Jake Moore commented that though the shortlinked service seemed sensible at first glance, little thought appeared to have been put into properly securing it: “The problems often lie when such processes are innocently created by individuals who fail to test the application with a criminal mindset. It is vital that processes are designed with the help of people trying to [illicitly] hack them or at least an illicit approach is taken into account in order to fully test them.”
‘We take this very seriously’
Councils responsible for the personal data exposure were hardly apologetic when The Register asked what they had to say for themselves.
A Cardiff Council spokesman said the local authority “takes the processing of personal data and Data Protection legislation extremely seriously, and the concerns raised have been reported to the Data Protection Officer to be investigated, in line with the Council’s Data Protection policy and procedure.”
A spokesman confirmed that the council had carried out a Data Protection Impact Assessment before using Telsolutions.
Coventry City Council told us: “Telsolutions is used by a number of local authorities and throughout the debt recovery industry. Telsolutions confirm that late in 2020 they discovered an issue with their system which potentially enabled people to access details about council tax payers even if they were not the recipient of such a reminder. In order to access the information a person would need to obtain the postcode for the intended recipient.”
The spokesman went on to say “the majority of links sent [were] not being accessed at all”, adding that the council “takes very seriously its data protection obligations and works with its numerous suppliers to ensure that our residents’ data is protected.”
Capita, responding on behalf of Barnet, Bexley and Lambeth councils (the mega-outsourcer has a contract for collecting taxes on behalf of these local authorities) said: “A technical issue was uncovered with a service that is administered with the support of a specialist supplier. We regard the security of our clients’ data with the highest importance and we are working closely with all parties to resolve and investigate this error as quickly as possible.”
Southampton City Council said it “takes the protection of our customers’ data very seriously and is now investigating this issue.”
Walsall Council confirmed it uses Telsolutions and said it “takes its data protection obligations very seriously and works closely with suppliers to ensure that our residents data is protected and immediate action takes place to protect our customers if an issue is identified.”
Greenwich Council acknowledged receipt of our request for comment but did not comment.
Brighton and Southwark Councils failed to respond to requests for comment last week. ®
READ MORE HERE