The evolution of Microsoft Threat Protection, June update
Since our announcement of Microsoft Threat Protection at Microsoft Ignite, our goal has been to execute and deliver on our promise of helping organizations protect themselves from today’s sophisticated and complex threat landscape. As we close out our fiscal year, we’ve continued progress on developing Microsoft Threat Protection, launching new capabilities and services. Hopefully, you’ve had a chance to follow our monthly updates.
As we previously shared, Microsoft Threat Protection enables your organization to:
This month, we want to share new capabilities that are starting public previews.
Efficient remediation and response for identity threats
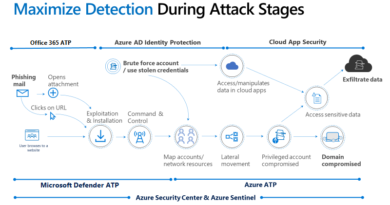
Presently, efficient and effective response to identity threats is crucial, and Microsoft Threat Protection is built on the industry’s most widely used and comprehensive identity security service. As more organizations adopt hybrid environments, data is spread across multiple applications, is on-premises and in the cloud, and is accessed by multiple devices (often personal devices) and users. Most organizations no longer have a defined network perimeter, making traditional security tools obsolete. Identity is the control plane that is consistent across all elements of the modern organization.
At RSA, we announced a new unified Identity Threat Investigation experience between Azure Active Directory (Azure AD) Identity Protection, Azure Advanced Threat Protection (ATP), and Microsoft Cloud App Security. This experience will go into public preview this month.
Part of the new experience is enabled through Azure AD’s new integration with Azure ATP. Also, integration between Azure AD and Microsoft Cloud App Security enables continuous monitoring of user behavior from sign-in through the entire session. Microsoft Threat Protection’s identity services leverage user behavior analytics to create a dynamic investigation priority score (Figure 1) based off signal from Azure AD, Microsoft Cloud App Security, and Azure ATP. The investigation priority is calculated by assessing security alerts, abnormal activities, and potential business and asset impact related to each user. This score can help Security Operations (SecOps) teams focus and respond to the top user threats in the organization.
Figure 1. The investigation priority view.
To learn more, read Investigating identity threats in hybrid cloud environments.
Game-changing capabilities for endpoint security
Every month, Microsoft Threat Protection detects over 5 billion endpoint threats through its Microsoft Defender ATP service. Customers have long asked us to extend our industry-leading endpoint security beyond the Windows OS. This was a major driving force for us to deliver endpoint security natively for macOS in limited preview earlier this year. We’re excited to announce that Microsoft Defender ATP for macOS is in public preview.
Microsoft Threat Protection customers who have turned on the Microsoft Defender ATP preview features can access Microsoft Defender ATP for Mac via the onboarding section in the Microsoft Defender Security Center. For more information and resources, including system requirements, prerequisites, and a list of improvements and new features, check out the Microsoft Defender ATP for Mac documentation.
To further enhance your endpoint security, “live response,” our new incident response action for SecOps teams, is currently in public preview. Today, your employees often work beyond the corporate network boundary, whether from home or while traveling. The risk for compromise is potentially higher when a user is remote. Imagine the executive who connects their laptop to hotel Wi-Fi and is compromised. With current endpoint security services, SecOps would need to wait until the executive got back to the office, leaving a high-value laptop exposed. With our new live response, SecOps teams gain instant access to a compromised machine regardless of location, as well as the ability to gather any required forensic information.
This powerful feature allows you to:
- Gather a snapshot of connections, drivers, scheduled tasks, and services, as well as search for specific files or request file analysis to reach a verdict (clean, malicious, or suspicious).
- Download malware files for reverse-engineering.
- Create a tenant-level library of forensic tools like PowerShell scripts and third-party binaries that allows SecOps to gather forensic information like the MFT table, firewall logs, event logs, process memory dumps, and more.
- Run remediation activities such as quarantine file, stop process, remove registry, remove scheduled task, and more.
To learn more, try the live response DIY or read Investigate entities on machines using live response.
Figure 2. Run remediation commands.
Experience the evolution of Microsoft Threat Protection
Take a moment to learn more about Microsoft Threat Protection, read our previous monthly updates, and visit the Microsoft Threat Protection webpage. Organizations, like Telit, have already transitioned to Microsoft Threat Protection and our partners are also leveraging its powerful capabilities.
Begin a trial of Microsoft Threat Protection services, which also includes our newly launched SIEM, Azure Sentinel, to experience the benefits of the most comprehensive, integrated, and secure threat protection solution for the modern workplace.
READ MORE HERE