Mobile security—the 60 percent problem

Off the top of your head, what percentage of endpoints in your organization are currently protected?
Something in the 98 percent+ range?
Most enterprises would say having fewer than 2 percent of endpoint devices lacking adequate security would be considered good given the various changes, updates, etc. However, enterprises have traditionally focused security and compliance efforts on traditional computing devices (for example, servers, desktops, and laptops), which represent just 40 percent of the relevant endpoints. The remaining 60 percent of endpoints are mobile devices and are woefully under-protected. That’s a problem.
Mobile security is more important than ever
Mobile devices, both corporate-owned and bring your own device (BYOD), are now the dominant productivity platform in any enterprise organization, with more than 80 percent of daily work performed on a mobile device. These devices operate extensively outside of corporate firewalls, in the hands of users who may not prioritize precautions like vetting Wi-Fi networks or keeping their devices patched and updated. Mobile often represents a wandering corporate data repository.
These factors combine to cause headaches for security teams because, in short, mobile security has a significant gap in most organizations’ endpoint protection strategies.
The lack of protection for (and visibility into) these endpoints introduces significant risk and compliance concerns that show no sign of slowing down. Here are some statistics from Zimperium’s State of Enterprise Mobile Security Report, 2019, which contains data from more than 45 million anonymized endpoints from enterprises in a variety of industries and both local and national government agencies from around the world:
- Mobile OS vendors created patches for 1,161 security vulnerabilities in 2019.
- At the end of 2019, 48 percent of iOS devices were more than four versions behind the latest OS version and 58 percent of Android devices were more than two versions behind.
- Twenty-four percent of enterprise mobile endpoints were exposed to device threats, not including outdated operating systems.
- Nineteen percent of enterprise mobile endpoints experienced network-based attacks.
- Sixty-eight percent of malicious profiles were considered “high-risk,” meaning they had elevated access that could lead to data exfiltration or full compromise.
Microsoft and Zimperium deliver comprehensive mobile security
The combination of Microsoft’s management and security solutions and Zimperium’s unique on-device mobile device security delivers unequaled protection for managed and unmanaged BYOD devices. Together, Microsoft and Zimperium have delivered numerous innovations for customers in areas such as:
An endpoint is an endpoint is an endpoint, and they all must be protected
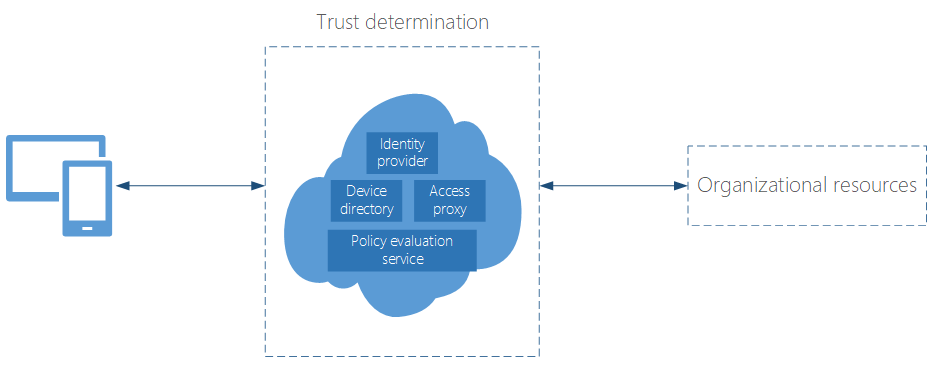
Organizations now realize mobile devices are an unprotected endpoint with possible access to or containing the information of a traditional endpoint. And while there are some overlaps in what you protect—email, calendars, etc.—the way you solve the traditional endpoint security problem is completely different than how you solve the mobile security problem.
So, what does all this really mean for an enterprise?
For a joint Microsoft and Zimperium international banking customer with employees in nine countries using 17,000 corporate and BYOD mobile devices, it means knowing that you are protected with Microsoft Endpoint Manager on Azure. It means knowing how many of your employees are putting your enterprise at risk with outdated iOS versions and high-risk profiles. It means having the ability to remediate and monitor your endpoints with one console. Our customer is in control of its infrastructure choices versus having the vendor forcing a solution. In addition, both iOS and Android platforms are supported and protected. If a user were to switch from one device to another that runs a different OS, the person would simply re-download the Zimperium app and activate.
Once deployed, the solution is capable of simultaneously integrating with unified endpoint solutions (UEM) solutions from multiple vendors. In other words, part of the organization, or specified users, can be managed with one UEM solution, and part of it by another. For joint Zimperium and Microsoft customers, this capability simplifies the migration from a third-party UEM to Microsoft Endpoint Manager while maintaining security during the migration. Zimperium provides visibility and security across the mobile infrastructure for customers who may have multiple UEM solutions deployed.
About Zimperium
Zimperium, the global leader in mobile device and app security, offers real-time, on-device protection against Android and iOS threats. The Zimperium platform leverages our award-winning machine-learning-based engine—z9—to protect mobile data, apps, and sessions against device compromises, network attacks, phishing attempts, and malicious apps.
To date, z9 has detected 100 percent of zero-day device exploits without requiring an update or suffering from the delays and limitations of cloud-based detection—something no other mobile security provider can claim.
Get a free enterprise trial
Interested in trying Zimperium in your Microsoft security environment? Contact us today for mobile device security with protection against network, device, phishing, and malicious app attacks.
READ MORE HERE