NetDooka Framework Distributed via PrivateLoader Malware as Part of Pay-Per-Install Service
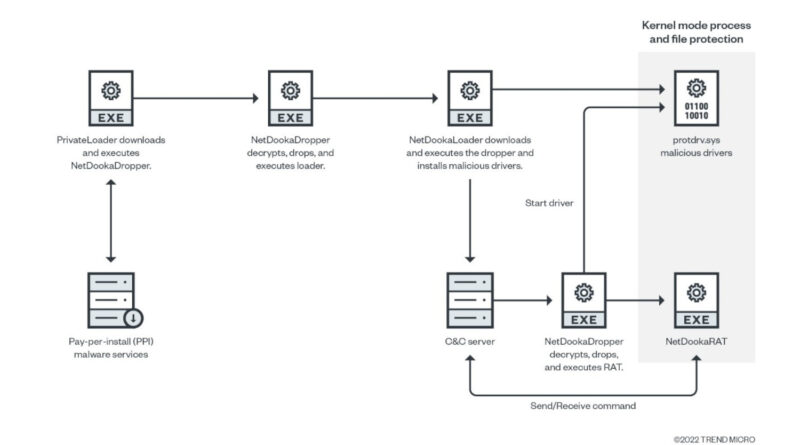
This report focuses on the components and infection chain of the NetDooka framework. Its scope ranges from the release of the first payload up until the release of the final RAT that is protected by a kernel driver. Read More HERE…