This Week in Security News – February 11, 2022


Read on:
Hidden Scams in Malicious Scans: How to Use QR Codes Safely
The practical approach to life after COVID-19 is for people to learn to live with it and do what they can to manage it. One of the things that is likely to remain for the foreseeable future is the need for cashless and no-contact transactions. Many businesses have responded to this need through the use of quick response (QR) codes, however threats involving QR codes have become so rife and sly that the FBI has recently issued a warning about them.
Feds Arrest Couple Who Allegedly Laundered $1 Billion in Stolen Bitcoins
The Department of Justice announced the arrests and indictment of Russian-U.S. national Ilya Lichtenstein, 34, and his wife, Heather Morgan, 31, in a press release. Prosecutors accused Lichtenstein and Morgan of attempting to launder almost 120,000 BTC (currently worth around $5 billion) through a wallet owned by Lichtenstein.
The LockBit intrusion set, tracked by Trend Micro as Water Selkie, has one of the most active ransomware operations today. With LockBit’s strong malware capabilities and affiliate program, organizations should keep abreast of its machinations to effectively spot risks and defend against attacks. Trend Micro analyzes what organizations need to know about LockBit, their impact, affected industries and more in this Ransomware Spotlight.
Microsoft Considering Possible Deal for Mandiant
Microsoft Corp. is in talks to acquire cybersecurity research and incident response company Mandiant Inc., a deal that would bolster efforts to protect customers from hacks and breaches, though the deliberations may not result in an offer.
Why Cyber Change Outpaces Boardroom Engagement
In cybersecurity, a recurring narrative is one of C-suite executives perpetually at odds with IT leaders. They’re disinterested in what the security team does, and release funds begrudgingly and often reactively once a serious incident has occurred. This leads to mounting cyber risk, and an increasing likelihood that the organization will suffer serious reputational and financial damage stemming from future incidents—or so the story goes. Closer IT-board engagement is a must if these organizations are to avoid the mistakes of the past and build a security-by-design culture that permeates enterprise-wide.
Iranian Hackers Using New Marlin Backdoor in ‘Out to Sea’ Espionage Campaign
An advanced persistent threat (APT) group with ties to Iran has refreshed its malware toolset to include a new backdoor dubbed Marlin as part of a long-running espionage campaign that started in April 2018. Slovak cybersecurity company ESET attributed the attacks — codenamed “Out to Sea” — to a threat actor called OilRig, while also conclusively connecting its activities to a second Iranian group tracked under the name Lyceum.
Suspected Chinese Hackers Hit News Corp with ‘Persistent Cyberattack’
Dozens of journalists at the News Corp-owned Wall Street Journal were targeted in the hack, which appeared to focus on reporters and editors covering China-related issues, two people familiar with the matter told CNN. Cybersecurity firm Mandiant believes the hackers are “likely involved in espionage activities to collect intelligence to benefit China’s interests.”
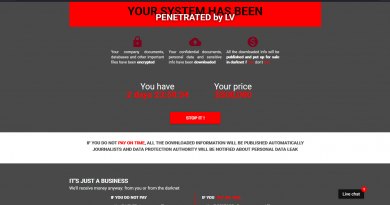
A Sign of Ransomware Growth: Gangs Now Arbitrate Disputes
The new report on 2021 ransomware trends highlights the growing maturity and specialization of the ransomware market, with independent operators filling a lucrative niche market. Specialists now range from the hackers who can break into networks or develop ransomware to the nontechnical operators who negotiate payments with victims. The United Kingdom’s National Cyber Security Centre said it’s seen some ransomware gangs offer a 24/7 help center to victims to expedite ransom payments and restore encrypted data.
Have you come across any suspicious QR codes? Share in the comments below or follow me on Twitter to continue the conversation: @JonLClay.
Read More HERE