Malvertising Used as Entry Vector for BlackCat, Actors Also Leverage SpyBoy Terminator
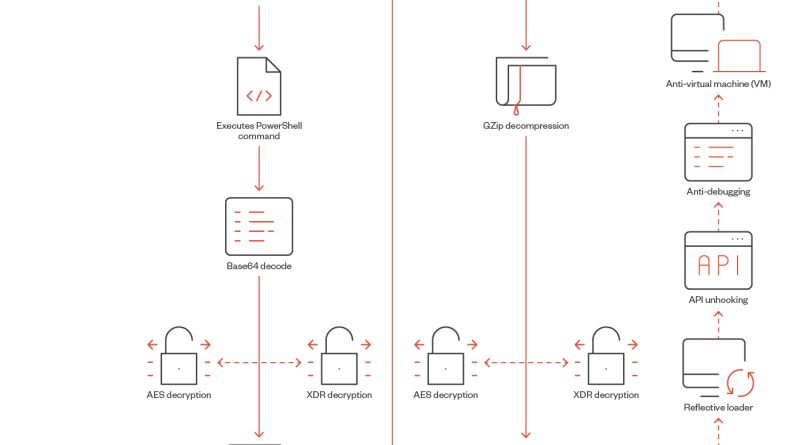
We found that malicious actors used malvertising to distribute malware via cloned webpages of legitimate organizations. The distribution involved a webpage of the well-known application WinSCP, an open-source Windows application for file transfer. We were able to identify that this activity led to a BlackCat (aka ALPHV) infection, and actors also used SpyBoy, a terminator that tampers with protection provided by agents. Read More HERE…