Earth Kitsune Delivers New WhiskerSpy Backdoor via Watering Hole Attack
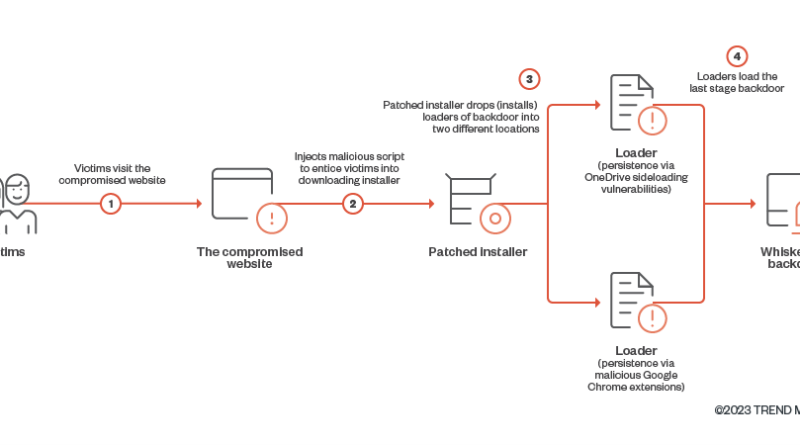
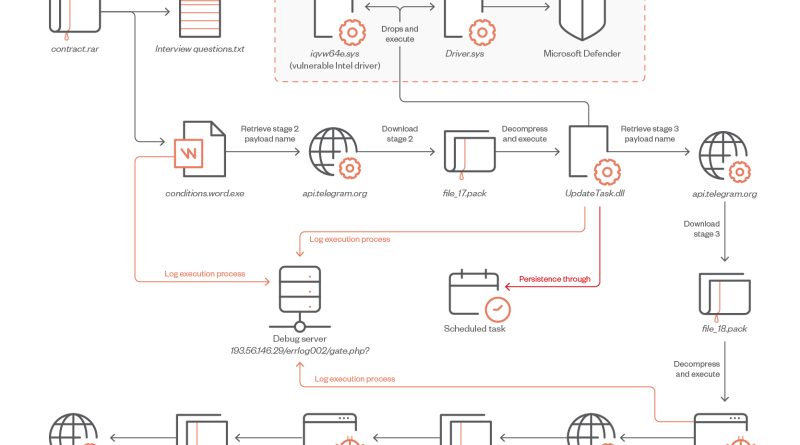
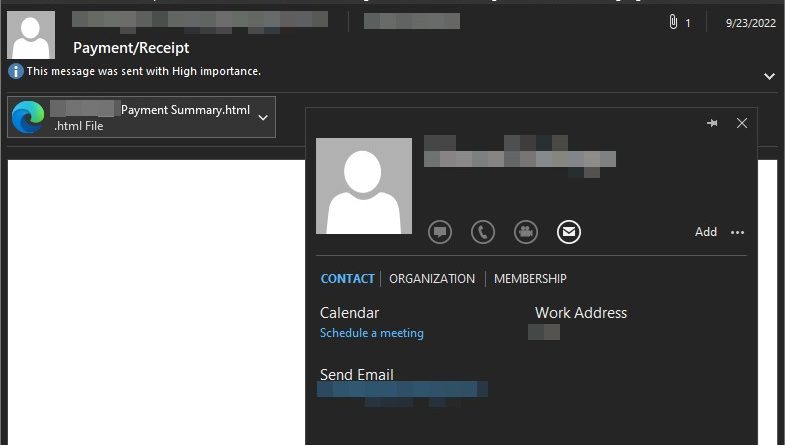
We discovered a new backdoor which we have attributed to the advanced persistent threat actor known as Earth Kitsune, which we have covered before. Since 2019, Earth Kitsune has been distributing variants of self-developed backdoors to targets, primarily individuals who are interested in North Korea. Read More HERE…