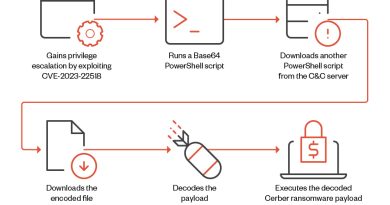
Ransomware Actor Abuses Genshin Impact Anti-Cheat Driver to Kill Antivirus


The mhyprot2.sys driver that was found in this sequence was the one built in August 2020. Going back to social media streams, we can see that shortly after Genshin Impact was released in September 2020, this module was discussed in the gaming community because it was not removed even after the game was uninstalled and because it allowed bypassing of privileges.
A PoC, provided by user kagurazakasanae, showed that a library terminated 360 Total Security. A more comprehensive PoC, provided by Kento Oki, had the following capabilities:
- Read/Write any kernel memory with privilege of kernel from user mode.
- Read/Write any user memory with privilege of kernel from user mode.
- Enumerate a number of modules by specific process id.
- Get system uptime.
- Enumerate threads in a specific process, allowing reading of the PETHREAD structure in the kernel directly from the command-line interface (CLI).
- Terminate a specific process by process id with ZwTerminateProcess, which calls in the vulnerable driver context (ring-0).
The issue was also reported by Kento Oki to miHoYo, the developer of Genshin Impact, as a vulnerability. Kento Oki’s PoC led to more discussions, but the provider did not acknowledge the issue as a vulnerability and did not provide a fix. Of course, the code-signing certificate is still valid and has not been revoked until now and the digital signature for code signing as a device driver is still valid at this time.
Complications of code signing as a device driver
It is still rare to find a module with code signing as a device driver that can be abused. The point of this case is that a legitimate device driver module with valid code signing has the capability to bypass privileges from user mode to kernel mode. Even if a vendor acknowledges a privilege bypass as a vulnerability and provides a fix, the module cannot be erased once distributed. This file has a code signature for the driver, which allows this module to be loaded in kernel mode. If the signature was signed for a malicious module through private key theft, the certificate can be revoked to invalidate the signature. However, in this case, it is an abuse of a legitimate module. It seems that there is no compromise of the private key, so it is still not known if the certificate will be revoked. It remains valid, at least for now.
As mentioned above, this module is very easy to obtain and will be available to everyone until it is erased from existence. It could remain for a long time as a useful utility for bypassing privileges. Certificate revocation and antivirus detection might help to discourage the abuse, but there are no solutions at this time because it is a legitimate module.
How to counter abuse: monitoring and detection
There are only a limited number of driver files with valid signatures that are expected to have behavior comparable to the privilege bypassing we report here. We recommend that security teams and network defenders monitor the presence of the hash values within their organizations. We have confirmed that privilege bypassing is possible in at least this file:
- mhyprot2.sys (0466e90bf0e83b776ca8716e01d35a8a2e5f96d3)
In addition, we recommend monitoring Windows event logs for the installation of the service corresponding to the driver. If the installation of the service was not intended, compromise is strongly suspected:
- Windows Event Log (System) – 7045: A new service was installed in the system. Service name: mhyprot2.
Read More HERE