Review: SaltStack brings SecOps to network orchestration and automation
It’s clear from the first few moments working with the SaltStack platform that it began life as a network orchestration and automation platform. It elegantly brings hundreds of disparate systems together in one place, allowing administrators to parse and configure them however they want. More recently, SaltStack added what it calls SecOps modules over top of that excellent management platform. This adds cybersecurity to SaltStack’s already impressive capabilities, enabling security teams to detect and fix problems across an entire enterprise in just a few minutes.
For this review, we examined SaltStack Enterprise version 6.1 running in a demo environment consisting of several systems with various operating platforms as well as quite a few network devices. There were two of the newer SecOps modules active during the testing, SaltStack Comply and SaltStack Protect.
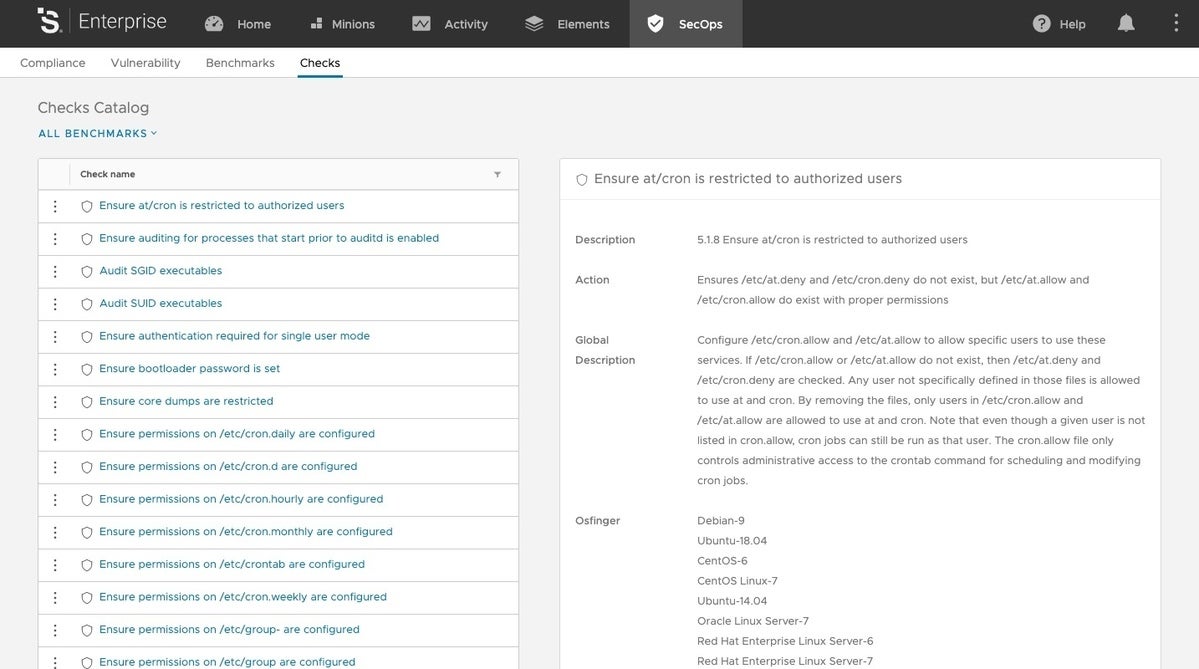
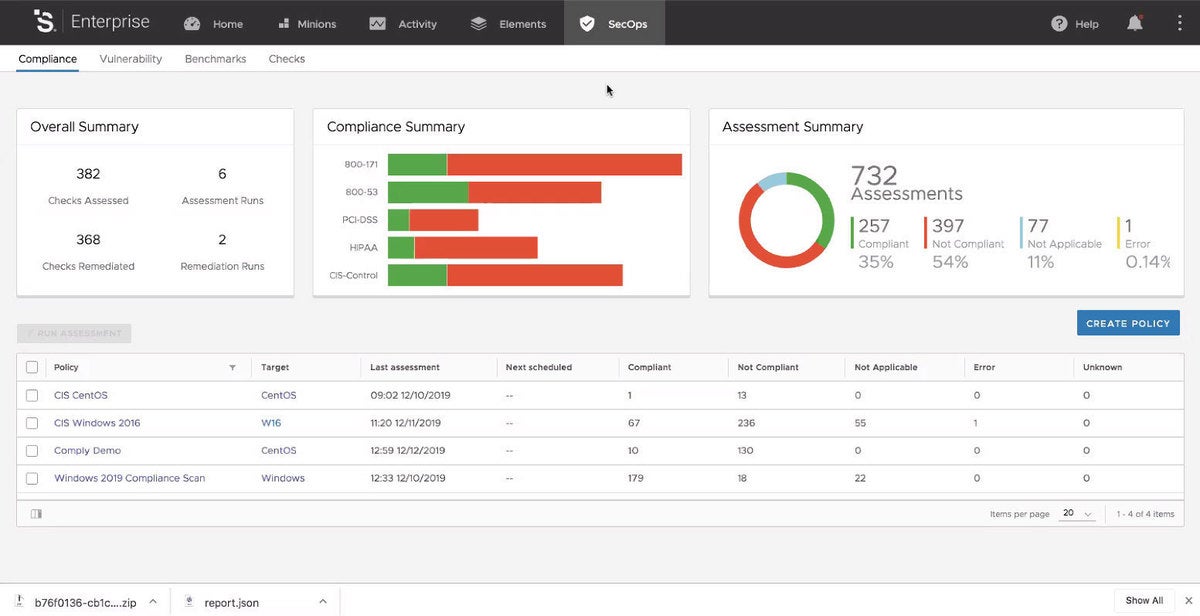
SaltStack Comply gives access to a growing repository of compliance standards and allows administrators to scan for any compliance issues across an enterprise. If any are located, the orchestration capabilities of the main SaltStack program allow for rapid fixes and follow-up compliance checks and monitoring.
Many industries must legally comply with various policies and regulations. SaltStack can check all assets across an enterprise against many of the popular compliance frameworks. Organizations can also define their own compliance rules.
Log in or subscribe to Insider Pro to read the full review of SaltStack Enterprise.
It’s clear from the first few moments working with the SaltStack platform that it began life as a network orchestration and automation platform. It elegantly brings hundreds of disparate systems together in one place, allowing administrators to parse and configure them however they want. More recently, SaltStack added what it calls SecOps modules over top of that excellent management platform. This adds cybersecurity to SaltStack’s already impressive capabilities, enabling security teams to detect and fix problems across an entire enterprise in just a few minutes.
For this review, we examined SaltStack Enterprise version 6.1 running in a demo environment consisting of several systems with various operating platforms as well as quite a few network devices. There were two of the newer SecOps modules active during the testing, SaltStack Comply and SaltStack Protect.
SaltStack Comply gives access to a growing repository of compliance standards and allows administrators to scan for any compliance issues across an enterprise. If any are located, the orchestration capabilities of the main SaltStack program allow for rapid fixes and follow-up compliance checks and monitoring.
Many industries must legally comply with various policies and regulations. SaltStack can check all assets across an enterprise against many of the popular compliance frameworks. Organizations can also define their own compliance rules.
The SaltStack Protect module imports vulnerability advisories from vendors and allows users to build custom scans of almost any equipment. It enables remediation of both vulnerabilities and cybersecurity problems by security teams. And it uses the same graphical SaltStack interface as the main enterprise program.
Most enterprises will have a lot going on with a SaltStack deployment, yet the main interface is both graphical and easy to use. And this interface is completely API-based, so users can ignore it and do everything with console commands if they prefer.
The setup
SaltStack Enterprise is deployed as an on-prem solution in two or more components. The brains of the operation can exist on almost any enterprise server with sufficient power to host the software. It can also sit on a virtual machine or in the cloud. The second part of SaltStack is the master traffic monitor component. Like the main server, the master traffic monitor can be deployed on any available hardware. The traffic monitor collects data from agents, parses it and sends reports to the main SaltStack server. This way, the main server is never overloaded by too many agents reporting in at the same time.
For a smaller enterprise, that is all that would be needed. However, one of the strengths of SaltStack is its ability to scale almost infinitely. To do that, more traffic monitors would be deployed, reporting back to the master traffic monitor, which in turn sends its data to the main server. SaltStack has customers who are managing close to 100,000 servers and network devices using this setup.
The platform relies on installing agents to client machines and devices. This gives SaltStack the ability to tightly control those endpoints and quickly make fixes. Agents, which SaltStack comically calls minions, can be deployed the traditional way as tiny programs that exist directly on an endpoint. SaltStack can also work in an agentless setup for some devices, though this gives less control and is not generally recommended. In that case, the minion is temporarily installed whenever the system needs to be scanned or configured, does its job and then disappears. For devices that require agents but aren’t able to host them, like a switch with no spare memory, they can be given a proxy agent where the minion sits on an external device but constantly monitors its target as if it were installed locally.
Minions are the clever way that SaltStack refers to its agents, which are deployed on assets to assert greater control over them. The minions’ page shows every agent managed by the platform and the groups of systems where they are assigned.
Whereas monitoring devices on an enterprise network can be done through the main graphical interface, currently minions can only be deployed using a command line interface. This may not be too big a deal for experienced security or operational teams, but could slow down deployment, especially for large networks.
In any case, pricing for SaltStack Enterprise is a subscription model that is based on the number of nodes being managed. Modules can be purchased separately or bunded with the main program.
Testing SaltStack
The first thing that most administrators will probably want to do with SaltStack Enterprise is to sort their network’s systems down into manageable groups. This is a very intuitive process with SaltStack, and also an important one since the most effective cybersecurity and compliance rules will be tightly targeted at relevant groups of systems.
For our test, we created a group that included every device in the testbed running the Linux-based CentOS by simply selecting that option from the dropdown menu of available systems. Once the group was created, SaltStack kept monitoring the enterprise. Whenever any new CentOS devices came online, they were automatically added to the group without further user intervention.
As an orchestration tool, it was not surprising to find that SaltStack could configure almost every nuance of each group. For example, we changed the required delay between password attempts to a longer period, which became policy on every device within that group.
The policy window displays information about security policies that the platform has been asked to track, as well as problems and vulnerabilities from the most recent scans.
You can then define the rules by which various users can interact with the groups you create. For example, we added a user named Skylar who could only scan the devices in the CentOS group to look for compliance issues. We created another user named Ivan who was able to actually remediate whatever issues Skylar discovered. In this way, SaltStack can enforce very tight role-based access controls. And it’s totally up to platform administrators how they sort and manage their network using SaltStack. The possible configurations are limitless.
When a vulnerability was discovered by the SaltStack Protect module in one of the managed groups, a report was generated in the main interface. If an administrator with sufficient permission agrees that a fix is needed, it can be done through SaltStack with the press of one button. The platform will fix the vulnerability, or even a compliance issue, on every single device within the target group. Fixes are just as easy to deploy across an entire enterprise.
The fixes are fast, too. It only took a couple minutes on our modest testbed to fix all instances of a discovered compliance issue. Because of the way SaltStack’s traffic monitoring devices and minions are deployed, it would not take that much longer to complete remediation tasks in a much larger enterprise. And any actions users take with the program are recorded, encrypted and stored to make for easy auditing.
All of these features make SaltStack Enterprise and its optional SecOps modules one of the only platforms available today that can fully manage complex enterprise environments while also protecting them. It can handle operational tasks like patch management and provisioning just as well as security functions like vulnerability and compliance testing. It could find a welcome home for SecOps teams working in any complex enterprise environment. And the more complex the network, the more SaltStack is probably needed.
READ MORE HERE