Ransomware Business Models: Future Pivots and Trends


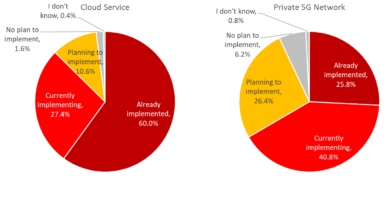
RDP port 3389 remains a popular service abused by ransomware actors to gain initial access to systems located and connected to on-premise infrastructure. However, as more organizations shift to the cloud services for file storage and active directory systems, ransomware groups will look for more opportunities to develop and/or exploit vulnerabilities not yet leveraged at scale.
Evolutions
Gradual evolutions in the current modern ransomware models as we know them are expected to be tweaked in order to adapt to the triggers that prompt them. From a business perspective, these are “naturally occurring” movements that prompt movement from their current state. In this section, we list two gradual evolutions that ransomware actors will likely be undergoing to adapt to the upcoming triggers in the short term. For the full list of evolutions and their respective discussions, you can download our paper here.
Evolution 1: Change of targeted endpoints – The internet of things (IoT)/Linux
The Mirai botnet, which emerged in 2016, was a decisive point that realized the possibility of expanding its reach to Linux devices and the cloud. While it’s not ransomware, the availability of the botnet’s source code allowed parties with the interest and skillset to simply download and recompile the code to infect Linux-based routers to create their own botnet. These address two points for this specific evolution:
- They have the code ready to target Linux-based devices and can simply recode for other similar devices.
- They are ready to use this capability as soon as there are visible targets with internet-facing security gaps.
From these two points, ransomware groups can find new Linux-based targets or tweak the threat they currently have at hand to target new platforms such as cloud infrastructures, prompting possible developments:
- Ransomware groups focus their sights on regular Linux servers
- Ransomware groups start targeting backup servers
- Ransomware groups start targeting other IoT Linux-based devices
With the increased use of Linux-based servers, the cloud, and — as another entry point — the internet of things (IoT), ransomware groups have realized an opportunity in attacks against these devices as endpoints. This is a potentially lucrative shift because:
- They are powerful enough to support highly functional capabilities.
- They are connected to the internet almost all the time.
- They host a plethora of valuable information, personal or otherwise.
- They are often vulnerable and unsupported.
In relation and as an example of this expansion, reports of attacks and abuse to network attached storage (NAS) devices are well-documented, but it would be underestimating threat groups to think they would stop there.
Evolution 2: Scale up through increased professionalism and automation
As RaaS groups gained more notoriety for the disruptions and losses they caused on organizations and users, some ransomware actors were giving interviews to the media. Unbeknownst to them, the interviewees’ RaaS infrastructure were already compromised and being monitored by security researchers as these ransomware actors talked to journalists.
While many RaaS groups have websites on Tor-hidden servers, security researchers and law enforcement found the clear web IP addresses of these attacks. This could imply that any unencrypted data stored on those backend servers will become easy targets for law enforcement.
Contrary to these notorious players, other ransomware actors have better OpSec, do not engage with the media, minimize their interactions with victims, and do not have documented intrusions of their network. If these notorious ransomware actors follow the examples of their lesser-known colleagues and remain under the radar while working with an increased level of professionalism, this can increase the longevity of their RaaS programs.
In the same vein, automating ransomware attacks will not only lessen the risks but also enable gangs’ scalability. While tailored, manual attacks have higher likelihoods of succeeding, more manual work means more risks because of the higher number of people required for tasks. Aside from the risks of human errors being made to the criminal operations, there have also been instances when disgruntled cybercriminals have doxed other cybercriminals or leaked information about them on the internet.
Automation, then, allows ransomware groups to calculate and weigh which channels will bring them more revenue: more automation might reduce revenue per ransomware victim, but it can also increase total revenue as far as targeted deployment quantities are concerned. There can also be lower costs and faster operations as affiliates responsible for initial access and lateral movement are subsequently cut out from the model because of automation, such as the use of mass exploitation or worm-like capabilities. Another avenue that can be replaced are ransom negotiators being replaced by automated chatbots, for instance, reducing communication between the perpetrators and the victims. Once big game hunters have realized the benefits of automation in terms of risks and profit, they could begin gravitating more to implementing it.
Revolutions
The stacking of small evolutions can lead to larger changes among ransomware groups. Security researchers have already documented some of these revolutions, such as the change from profit-oriented attacks to becoming a part of nation state actors’ objectives, benefitting countries or their leaders and using ransomware as a smokescreen for their real intent. Other RaaS groups may be driven by the evolution of cloud adoption or that of exploits and vulnerabilities. Still others will be driven to more changes to criminal business models with the promise of higher profits. In this section, we discuss two revolutions that ransomware actors will likely adopt in the long run. For a full list of the revolutions and their respective discussions, download our insights and research here.
Revolution 1: Hack into cryptocurrency exchanges/Steal cryptocurrencies
Read More HERE