This Week in Security News – August 20, 2021 VP, Threat Intelligence


Welcome to our weekly roundup, where we share what you need to know about cybersecurity news and events that happened over the past few days. This week, learn about a fake Tokyo Olympics broadcast page used for spam. Also, read about T-Mobile’s customer data hack.
Read on:
Tokyo Olympics Leveraged in Cybercrime Attack
On July 19, just before the opening of the Tokyo Olympics, Trend Micro confirmed a case where a web page disguised as a TV broadcast schedule for the Tokyo Olympics was directing to a suspicious sports broadcast site. According to a Trend Micro survey, this suspicious sports broadcast site was directed to so-called “browser notification spam”, which allows users to be notified of browsers and displays malicious advertisements.
T-Mobile Confirms It was Hacked Again
This month, T-Mobile confirmed that it was hacked. The company launched an investigation after a hacker named “Subvirt” advertised allegedly stolen data on the popular hacking site Raid Forums. Allegedly, more than 100 million T-Mobile customer records were stolen and said to include International Mobile Subscriber Identity numbers, International Mobile Equipment Identity or IMEI numbers, phone numbers, customer names, PINs, dates of birth, Social Security and driver’s license numbers.
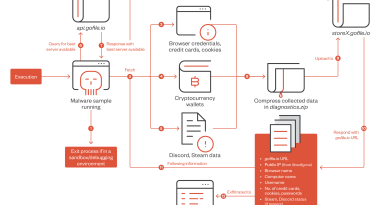
Fake Cryptocurrency Mining Apps Trick Victims into Watching Ads Paying for Subscription Service
Trend Micro recently discovered eight deceptive mobile apps that masquerade as cryptocurrency cloud mining applications where users can earn cryptocurrency by investing money into a cloud-mining operation. These malicious apps trick victims into watching ads, paying for subscription services that have an average monthly fee of US $15, and paying for increased mining capabilities without getting anything in return.
COVID-19 Contact-Tracing Data Exposed, Fake Vax Cards Circulate
The Indiana Department of Health issued a notice that the state’s COVID-19 contact-tracing system had been exposed via a cloud misconfiguration, revealing names, emails, gender, ethnicity, race and dates of birth of more than 750,000 people. The incident shows that COVID-19 data could be poised for abuse and misuse. Meanwhile, COVID-19 vaccine fraud is also on the rise — demonstrating that the pandemic still offers a rich vein for cybercriminals of all stripes to mine.
Confucius Uses Pegasus Spyware-Related Lures to Target Pakistani Military
While investigating the Confucius threat actor, Trend Micro found a recent spear phishing campaign that utilizes Pegasus spyware-related lures to entice victims into opening a malicious document downloading a file stealer. The NSO Group’s spyware spurred a collaborative investigation that found that it was being used to target high-ranking individuals in 11 different countries.
Now a Consortium to Prevent Cyberattacks on Connected Cars
Car makers Toyota, Hyundai and Nissan are forming a consortium that will aim to fight cyberattacks on connected cars and companies like Microsoft Japan, Trend Micro, NTT Communications, Sompo Japan Insurance are all set to join the campaign. The aim of the consortium will be to prevent hackers from hijacking autonomous vehicles and preventing data theft. As self-driving cars will pick up, OEMs should come up with cybersecurity measures that help protect the passengers.
LockBit Resurfaces with Version 2.0 Ransomware Detections in Chile, Italy, Taiwan, UK
The ransomware group LockBit resurfaced in June with LockBit 2.0, with reports indicating an increased number of targeted companies and the incorporation of double extortion features. Detections followed attack attempts in Chile, Italy, Taiwan, and the UK from July to August.
Top 4 Hybrid Cloud Systems Management Pain Points and How to Solve Them
The appeal of cloud computing is financial: rather than buying infrastructure, rent it. The problem with this financial solution is it distracts the cloud user from the responsibilities that remain after moving the applications out of the enterprise – responsibilities called systems management comprise IT Infrastructure and Operations, or I&O. This article reviews some of those functions considering a cloud migration.
A critical set of software flaws first revealed in April also affects code made by BlackBerry that is used in countless devices in the medical, automotive and energy sectors. The affected software is BlackBerry’s QNX Real-Time Operating System, a suite of software that manages data across a network. “These vulnerabilities may introduce risks for certain medical devices, as well as pharmaceutical or medical device manufacturing equipment,” the Food and Drug Administration said.
What are your thoughts on the T-Mobile hack? Share in the comments below or follow me on Twitter to continue the conversation: @JonLClay.
Read More HERE