How Should My Security Analyst Use the MITRE ATT&CK Framework?
Question: How should my security analyst use the MITRE ATT&CK Framework?
Yair Manor, Co-Founder and CTO, CardinalOps: As an analyst, ATT&CK lets you reason and communicate in a structured way about what an attacker may be trying to achieve and where they are in the kill chain. For example, is a particular alert related to an attacker establishing initial access or are they already exfiltrating data? Use ATT&CK as a standard language for communicating with your peers during investigations.
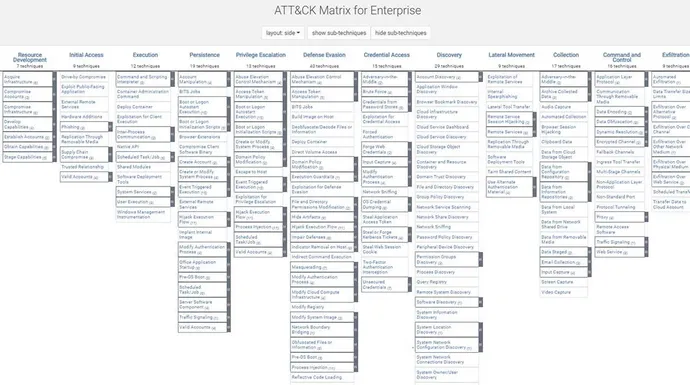
Use ATT&CK to guide your thinking on what to investigate next. If you see a Discovery technique being used, you may want to look for a Lateral Movement technique on that same machine, or perhaps look for Credential Access or Execution to understand how the attacker got onto the machine in the first place. Map each of your security tools and log sources to ATT&CK so you know the best tools to use for each asset type and each step in the kill chain.
Start by making sure you have detections for your most critical “crown jewel” assets and associated data sources, such as Windows, Linux, and cloud. You can’t check the box for “Persistence,” for example, until you’ve implemented coverage for all of them. If your organization is focusing on zero trust, make sure you’re also covering identity sources such as Active Directory and Okta. You can also prioritize detections based on techniques employed by specific APT and cybercriminal groups that target your industry.
Remember that new and emerging techniques don’t always map directly to the MITRE framework, so be sure to also monitor threat intelligence sources and implement detections as quickly as possible for the latest attack types (like Log4shell). Regularly report your current ATT&CK coverage to stakeholders and focus on continuous improvement over time, based on reducing risk to your crown jewel assets.
Read More HERE
