Cybersecurity Trends from the Global Pandemic

Although Agile deployment practices such as Agile, Scrum, Kanban, and many others have been around for years, the digital shift driven by the COVID-19 pandemic pushed many organizations to finally take these practices more seriously. The only way to keep up with a continuous demand for new features, running workloads at scale, and ensuring applications are resilient is through applying DevOps processes.
As developers and DevOps practitioners, you have to take on additional responsibilities to ensure your systems are secure. These include secrets management, source code security, container and VM security, and more.
Accelerated Movement to the Cloud
Migrating to the cloud is not a new phenominum. But during 2020 and 2021, organizations in the early stages of moving to the public cloud accelerated their move. Even companies who thought they could postpone this maneuver soon realized they must take action immediately.
Gartner forecasts that in the aftermath of the COVID-19 crisis, the worldwide end-user spending on public cloud services will grow 18.4 percent in 2021 to total $304.9 billion.This migration to the cloud means DevOps will only continue to grow in importance, so we had better be prepared.
Rapidly Shifting to Remote Work
The pandemic forced organizations worldwide to shift everyone to remote work. Employees had to perform as many business activities as possible remotely. Most organizations weren’t ready for this change.
With the rapid-paced movement to public cloud environments, DevOps teams need to migrate trusted on-premise tools to the cloud without compromising security. One major challenge to collaboration and remote work is determining where to store application source code.
Yes, we have distributed source control solutions based on Git (GitHub, Bitbucket, GitLab, and the like), but not all organizations use public cloud services. Many run Git in the company’s centralized data center using tools like GitHub Enterprise Server and Azure DevOps Server.
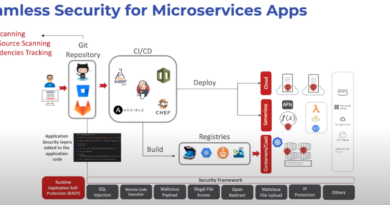
But we can move our source to the cloud without compromising security. Major providers like GitHub offer encryption and robust access control to ensure private code remains private. And source scanning tools like Trend Micro Cloud One™ – Open Source Security by Snyk provide additional protection by scanning your dependencies to find vulnerabilities.
Put simply, shifting left in our DevOps processes allows us to put security first — and it works just as well in the cloud as it does on-premise.
Supporting a Geographically Dispersed Workforce
Remote working and interconnecting sites involve building out a scalable VPN network. While many organizations already used VPNs before the pandemic, access was usually only available to a limited set of users.
Almost everyone now works from home, and connecting through the VPN introduces one more layer of complexity. Developers and DevOps must now test and deploy internal corporate apps to ensure they are all fully accessible via the company’s VPN.
One significant benefit of moving to the cloud is the ease of access. All employees can access line-of-business apps in the cloud without first connecting to the corporate VPN. However, this cloud availability introduces security risks such as malware and distributed denial-of-service (DDOS) attacks. We’ll explore these risks in the next section.
Expanding Security Concerns
As organizations embrace the cloud, they face new security concerns. Security must be top of mind for developers and DevOps professionals because you’re the ones writing, deploying, and maintaining your organization’s cloud applications.
Let’s consider some specific workload scenarios on top of the movement to the cloud. When deploying virtual machines, we’re in control of (but also taking responsibility for) network security (firewall and WAF-integrated load balancers) and virtual host protection (anti-malware tools).
Although we typically can’t control much of the runtime-host environment, a source code analysis tool is still beneficial when using a platform as a service. Storage solutions, which used to run on on-premises server farms and SAN/NAS appliances, can now shift to cloud-based storage solutions like Amazon Simple Storage Service (S3), Azure Blob storage, and the like.
When using containers like Docker or Kubernetes as a service with Amazon Elastic Kubernetes Service (EKS), Azure Kubernetes Service (AKS), Google Kubernetes Engine (GKE), or RedHat OpenShift, you should integrate a container vulnerability scanning tool as part of your process. These tools are necessary to tackle common container security vulnerabilities such as public container images, often containing outdated (thus vulnerable) packages and regularly having hard-coded secrets inside the images. Trend Micro’s container image security and registry scanning can help secure your containerized workloads.
Runtime Environments and Security Observability
We have already touched on the various hybrid and multi-cloud platform scenarios available to run your workloads, ranging from virtual machines to platform-as-a-service solutions to containerized workloads. No matter what architecture you put into place, your DevOps teams should always access end-to-end workload observability metrics, dashboards, and logs.
These metrics should primarily include and represent runtime data (indicating workload health) and allow for a complete security-state-view of those workloads. Trend Micro has teamed up with New Relic to provide this integration, relying on cloud connectors to centralize data and security information, and taking the necessary actions to mitigate cybersecurity threats.
As we’ve mentioned, the “shift left” approach, which moves security considerations and protection close to the start of the DevOps process, should become a priority. Security should include vulnerability scanning tools for source control code, keeping secrets and other confidential strings away from the source code, integrating container vulnerability scanning, and more. Many tools in the Trend Micro Cloud One platform, such as Container Security and Workload Security, check to ensure you haven’t accidentally introduced vulnerabilities to our apps or embedded credentials and other secrets in your code.
Summary
The pandemic has impacted the way organizations work. This shift to online solutions triggers a greater risk of cyberattacks than ever, so companies must prioritize safety.
Trend Micro Cloud One is a security services platform for cloud builders. Delivering the broadest and deepest cloud security offering in one solution, enabling you to secure your cloud infrastructure with clarity and simplicity. Try it out for free for 30 days!
Read More HERE