What is phishing? Learn how this attack works

Phishing is a method of trying to gather personal information using deceptive e-mails and websites. Stay tuned for what you need to know about this increasingly sophisticated form of cyberattack.
The goal of phishing is to trick an email recipient into believing that the message is something they want or need — a request from their bank, for instance, or a note from someone in their company — and to click a link or download an attachment.
“Phish” is pronounced just like it’s spelled, which is to say like the word “fish” — the analogy is of an angler throwing a baited hook out there (the phishing email) and hoping you bite.
What really distinguishes phishing is that attackers masquerade as a trusted entity of some kind, often a real — or plausibly real — person, or a company the victim might do business with. It might be your boss, your bank or a company whose software you use.
Perhaps one of the most consequential phishing attacks in history happened in 2016, when Russian hackers managed to get Hillary Clinton’s campaign chair John Podesta to offer up the password to his personal Gmail account. How did they do it? The hackers sent an email warning Mr. Podesta that someone had his password and that he should change it immediately. Clicking on a link in the email took him to a fake log-in page.
This is a classic ploy and one all of us hope we would see for what it is.
But email scammers are constantly honing their craft, trying new pitches and pulling new strings.
One way to get familiar with their tactics is to study the email messages that scammers send.
Here are a few real-world examples and how they work:
1. Your account has been hacked
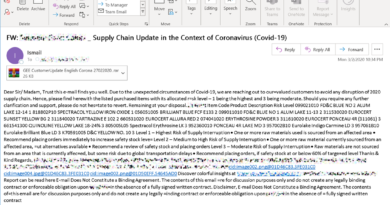
The person sending this threatening phishing message found a group email that was publicly available on the company website. Using that list to target the message was smart. Not so smart was the content of the message, in which the would-be attacker reveals a lack of understanding of how malware works.
2. Password reset
Taking advantage of the fact that no one wants to miss a paycheck, messages like this one aim to trick the user into revealing important data — often a username and password that the attacker can use to breach a system or account.
3. Payment request
This email has enough information specific to the target company to give even the most phishing-savvy recipients pause. The key to not getting caught in this trap is to know your company’s processes and be able to spot anomalies.
4. Charity donation
Here the scammer is counting on the greed and gullibility of the recipient. This theme of giving something away for free is a common one and preys on human nature. The key thing to remember is if it sounds too good to be true, it probably is.
Thanks for watching and stay safe out there!
READ MORE HERE