WA Auditor-General drags local governments over horrendous cyber risk management

Perth city
Image: Getty ImagesThe Western Australia Auditor-General has slammed local government (LG) entities in the hard border state, after determining they were not managing cyber risks well.
The outcome of the audit was summed up by two key findings noted in the audit report. The first was most vulnerabilities found during black box testing were over a year old, and in one instance, a vulnerability had existed for a decade and a half.
“We tested the audited LG entities’ publicly accessible IT infrastructure and found vulnerabilities of varying types, severity, and age. The vulnerabilities included disclosure of technical information, out-of-date software, flawed or weak encryption, insecure software configuration, and passwords sent in cleartext over the internet,” it said.
“44% of vulnerabilities were of critical and high severity, with a further 49% of medium severity.
“Known critical and high severity vulnerabilities are generally easy to exploit and expose LG entities to increased risk of compromise.”
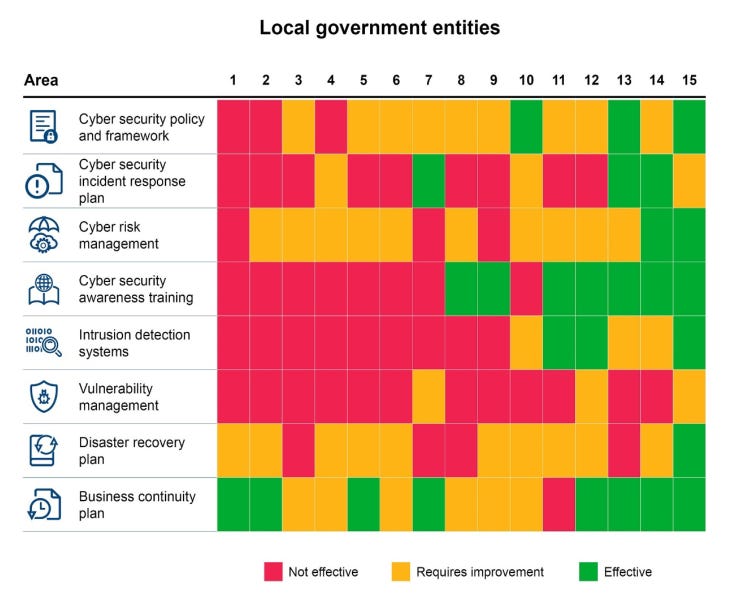
This is not good
Image: Office of the Auditor General for Western AustraliaThe AG found out-of-date software accounted for 55% of vulnerabilities, followed by weak or flawed encryption on 34%, and insecure configuration on 8% of vulnerabilities.
The second key finding was a phishing test, which led users to a page that asked them for login credentials. At one entity, over 50 people clicked the link, and around 45 submitted credentials, this was a result of one of the people selected for the phishing test forwarding it onto other staff and external contacts.
The AG said from that one forward action, it was able to collect 29 extra staff credentials that fell outside its intended testing scope, and 15 credentials from those external to the entity.
The number of click and credentials collected was around 5 to 10 times higher than the next highest number from an audited entity.
“[This] shows that people generally trust and are more likely to respond to emails from known contacts,” the report said.
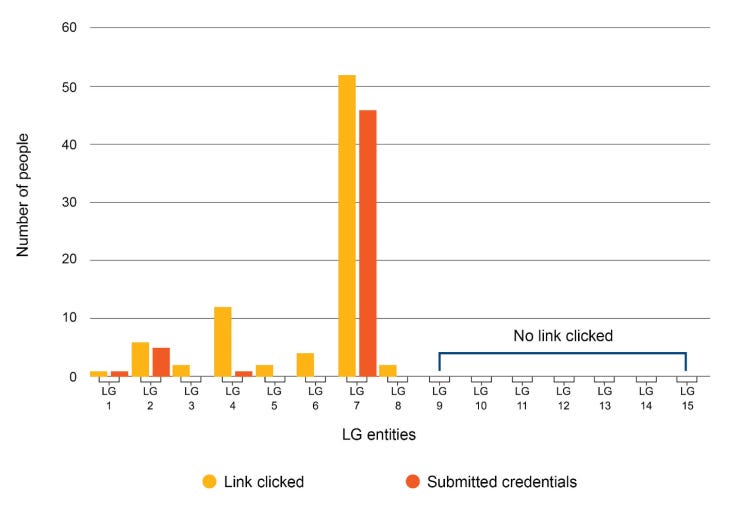
This is bad
Image: Office of the Auditor General for Western AustraliaMore generally, the report said the entities were found to have failed to consider the risks of malware and ransomware, data breaches including reuse of credentials found in other breaches, unauthorised access to systems or networks from an external attack, theft of IT devices, and third-party supply chain/cloud risks.
Two entities were found to have not had a penetration test done since 2015, while one entity never had.
When doing its tests, the Auditor-General found only three entities had systems to detect and block simulated attacks, while nine did not detect or respond, and three took two weeks to detect and only once the attacks ramped up. The latter 12 entities had intrusion detection systems but had no processes to look at the information generated in a timely manner, the AG said.
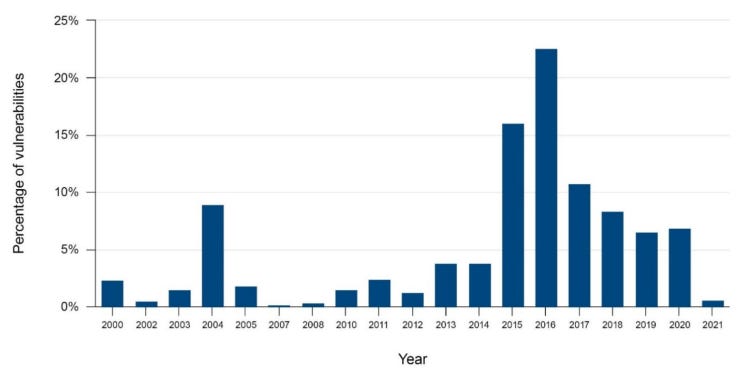
Yikes!
Image: Office of the Auditor General for Western AustraliaSeven recommendations were made to improve the entities’ cyber posture, which the AG said were “generally accepted”, and most had made improvements during the audit process.
“Entities should give regard to good practice principles in the Australian Government Information Security Manual and the Essential Eight controls to protect systems and information,” the report said.
“While remediations will require an investment of time and money, support from senior management is equally important to uplift cybersecurity maturity.”
Related Coverage
READ MORE HERE
