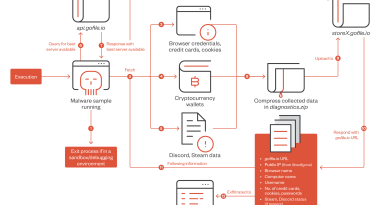
Void Rabisu Targets Female Political Leaders with New Slimmed-Down ROMCOM Variant

Void Rabisu is an intrusion set associated with both financially motivated ransomware attacks and targeted campaigns on Ukraine and countries supporting Ukraine. Among the threat actor’s previous targets were the Ukrainian government and military, their energy and water utility sectors, EU politicians, spokespersons of a certain EU government, and security conference participants. In campaigns conducted in late June and early August 2023, Void Rabisu targeted EU military personnel and political leaders working on gender equality initiatives. Among the notable tools used by Void Rabisu is the ROMCOM backdoor, of which it seems to be the exclusive user. ROMCOM itself has gone through various developments over time, including the implementation of more effective detection evasion techniques.
Void Rabisu is one of the clearest examples where we see a mix of the typical tactics, techniques, and procedures (TTPs) used by cybercriminal threat actors and TTPs used by nation-state-sponsored threat actors motivated primarily by espionage goals. For example, Void Rabisu has been signing malware with certificates most likely bought from a third-party service provider that other cybercriminal groups are also using. The threat actor has also employed malicious advertisements on both Google and Bing to generate search engine traffic to their lure sites, which contain malicious copies of software often used by system administrators.
Void Rabisu also acts like an advanced persistent threat (APT) actor when it targets governments and military. In June 2023, Void Rabisu exploited the vulnerability CVE-2023-36884 — still a zero-day vulnerability then — in campaigns using the Ukrainian World Congress and the July 2023 NATO summit as lures. The extraordinary geopolitical circumstances surrounding the war in Ukraine drives some of the financial-seeking threat actors (including Void Rabisu) toward campaigns motivated by espionage.
As reported by Microsoft, Void Rabisu used a zero-day vulnerability related to CVE-2023-36884 in attacks targeting governments at the end of June 2023. Trend Micro’s telemetry further confirms that this campaign targeted the military, government personnel, and politicians in Europe.
The payload spread by Void Rabisu during this period differed from the ROMCOM backdoor we analyzed in an earlier blog entry, but the two have clear similarities. This indicates that the threat actors are actively developing the ROMCOM backdoor.
The next iteration of the malware was used in early August 2023. On or around Aug. 8, 2023, Void Rabisu set up a malicious copy of the official website of the Women Political Leaders (WPL) Summit that was held in Brussels from June 7 to 8, 2023. The final payload was a new version of ROMCOM backdoor that we have dubbed as “ROMCOM 4.0” (also known as PEAPOD).
Attended by people from all over the world, the WPL summit aims to improve gender equality in politics. Among the topics included in the 2023 Brussels conference were peace and security, war and oppression, disinformation, the war in Ukraine, the role of women in politics, and gender equality. Since many current and future political leaders had attended this conference, it presented an interesting target for espionage campaigns and served as a possible avenue for threat actors to gain an initial foothold in political organizations. It is therefore not surprising that Void Rabisu set up a campaign targeting WPL Summit 2023 attendees. Our telemetry provided concrete evidence that this campaign was aimed at targets working on gender equality in EU politics.
In some of its latest campaigns, Void Rabisu started using a new technique that has not previously been reported on. It involves a TLS-enforcing technique by the ROMCOM command-and-control (C&C) servers that can render the automated discovery of ROMCOM infrastructure more difficult. We observed Void Rabisu using this technique in a May 2023 ROMCOM campaign that spread a malicious copy of the legitimate PaperCut software, in which the C&C server ignored requests that were not conformant.
This report provides a general background on Void Rabisu and its activities with regard to the recent WPL Summit campaign. We begin by describing how Void Rabisu targeted WPL Summit attendees in the following section.
On Aug. 8, 2023, Void Rabisu actors set up a website called wplsummit[.]com to attract visitors of the legitimate wplsummit.org domain. The fake website (shown in Figure 1) looked exactly like the legitimate one.
Read More HERE