Top Three Tactics for CISOs Facing Targeted Attacks


With targeted attacks showing no signs of slowing down, you need to ensure your organization is not only implementing the right security, but also following best practices, like network segmentation, analyzing network logs, and knowing when it is time to outsource incident response. Check out our recommendations for securing your network from targeted attacks and minimizing risk today, and in the future.
Securing the network from targeted attacks
Targeted attacks remain a serious risk to organizations, despite the continued advancement of security technologies. Many organizations still fall prey to targeted attacks because of the growing sophistication of tactics and tools cybercriminals use to stealthily breach the network.
In fact, a 2019 study conducted by Accenture and the Ponemon Institute shows that the average cost of cybercrime for each company—where sophisticated attacks are at play—has increased from US$11.7 million in 2017 to US$13.0 million in 2018.
Fortunately, you can still boost your defense strategy by complementing your cybersecurity solutions with best practices that can prevent targeted attacks and their devastating consequences. The following are three security recommendations that can protect your network from targeted attacks:
1. Implement Network Segmentation
When it comes to network infrastructure, a word that typically comes to mind is complexity, as it involves layers of users, workstations, servers, and connected devices. Complex networks pose challenges to security in terms of visibility and access management. To gain greater visibility, experts recommend breaking down individual components into ordered segments, which can be by department, location, or security level.
Network segmentation also prevents your employees from accessing parts of the network—and thereby digital assets—that should be restricted to them. This way, in the event of an attack, hackers and even insider threats can be prevented from accessing every part of your network—ultimately lowering your risk.
An important part of the network segmentation process is identifying critical assets that could cause your organization major damage if compromised. You need to determine which of your critical assets are most vulnerable to attacks and assign an appropriate level of security.
2. Analyze Your Network Logs—A Lot of Them
The collection and analysis of logs can help your organization detect targeted attacks and provide valuable information about the attackers. For example, with log analysis, you can better understand how attackers made their way into the network and their strategy (data exfiltration, corporate damage, etc.).
Logs can provide insights into your network’s general activity. By scanning for suspicious network activity, your security team can be more proactive when a suspected targeted attack is underway, and hopefully stop it before causing too much damage.
It is important to note that the use of logs can only be maximized by analyzing a large amount of them. Log analysis doesn’t only provide new threat intelligence; it also allows for the discovery of significant events in the network. Without an abundance of logs to analyze, a security professional can’t tell the whole story.
3. Establish a Cybersecurity Incident Response Team
In a perfect world, an organization would have an incident response team composed of cross-functional members from different departments who can deal with multiple concerns in the event of a targeted attack. The cybersecurity incident response team, in particular, should be separate from the regular IT team, and should be trained to address sophisticated attacks.
However, an in-house incident response team is becoming more difficult to assemble because of the widening cybersecurity skills gap. While some in-house IT staff members and security professionals are trained to manage and control the network, they may have minimal experience when it comes to targeted attacks. In addition, the lack of cybersecurity workers can overwhelm organizations—too many alerts, not enough staff.
Your best course of action to address this challenge is leveraging a third-party incident response team to help with your security needs. One type of service is managed detection and response (MDR), which gives organizations access to experienced cybersecurity professionals who can expertly perform a root cause analysis to get an understanding of:
- How attacks are initiated
- How far they spread in the network
- What remediation steps need to be taken
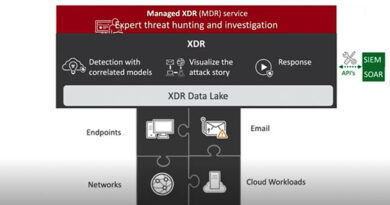
Trend Micro™ Managed XDR is one such service that offers a wider scope of visibility and expert security analytics by integrating detection and response functions across networks, endpoints, emails, servers, and cloud workloads. Using advanced analytics and artificial intelligence (AI) techniques, the Managed XDR team monitors your organization’s IT infrastructure 24/7 to correlate and prioritize alerts according to the level of severity.
With these three recommendations, you’ll be well on your way to gaining a clearer picture of the targeted attacks facing your organization, which is essential for better protection, faster remediation, and minimizing damage and risk.
Read More HERE