This Week in Security News – October 1, 2021 VP, Threat Intelligence


Welcome to our weekly roundup, where we share what you need to know about cybersecurity news and events that happened over the past few days. This week, learn about Zloader, a notable recent ZBOT variant. Also, read on a recently introduced bill that would mandate ransom payment reporting.
Read on:
IoT and Zero Trust Are Incompatible? Just the Opposite
With more IT and security becoming software-defined, Zero Trust is seen as a fundamental fix to the security approaches we’ve been struggling with. At first glance, the idea of ZT + IoT might seem incompatible, however, these innately untrusted, presumably insecure IoT devices are the perfect use case for why Zero Trust architectures are important for enterprise security.
Senators Introduce Cyber Bill to Mandate Reporting on Ransomware and Critical Infrastructure Attacks
If enacted, the bill will create the first national requirement for critical infrastructure entities to report when their systems have been breached. The legislation would require critical infrastructure owners and operators to report to the Cybersecurity and Infrastructure Security Agency within 72 hours if they are experiencing cyberattacks.
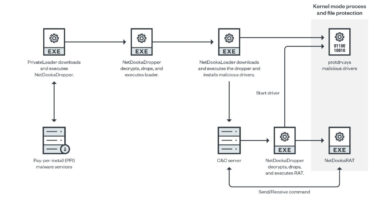
Fake Installers Drop Malware and Open Doors for Opportunistic Attackers
One way that attackers trick users is by luring them with unauthorized apps or installers carrying malicious payloads. These fake installers are not a new technique used by attackers; in fact, they are old and widely used lures that trick users into opening malicious documents or installing unwanted applications.
Cyberattacks Top List of Focuses for Business Leaders
Top of mind for companies are the volume and variety of attacks, cited by 49% and 43% of respondents, respectively. Privacy concerns (40%), greater reliance on data (38%) and quantifying security issues (34%) are other factors companies must account for when developing cybersecurity policies, implementing new practices and making investments.
FormBook Adds Latest Office 365 0-Day Vulnerability CVE-2021-40444 to Its Arsenal
Trend Micro detected a new campaign using a recent version of the known FormBook malware, an infostealer that has been around since 2016. Several analyses have been written about FormBook in the last few years, including the expanded support for macOS. FormBook is famous for highly obfuscated payloads and the use of document CVE exploitation.
Russia Detains Head of Cybersecurity Group on Treason Charges
The arrest comes after US President Joe Biden earlier this year raised concerns with Russian President Vladimir Putin that Moscow is allowing cybercrime directed at Western countries to flourish. Founded in 2003, the Group-IB group specializes in the detection and prevention of cyberattacks and works with Interpol and several other global institutions.
One of the most notable recent ZBOT variants is Zloader. Zloader has multiple delivery methods, such as via email campaigns or downloads by other malware and hacking tools. Its versatility has made it a popular and effective campaign tool for any threat actor that is willing to pay for it.
NSA, CISA Release Guidance on Hardening Remote Access Via VPN Solutions
The guidance suggests selecting only industry-standard solutions and not choosing non-standard VPN solutions, including a class of products referred to as Secure Sockets Layer/Transport Layer Security (SSL/TLS) VPNs. These products include custom, non-standard features to tunnel traffic via TLS.
IoT and Ransomware: A Recipe for Disruption
Ransomware attacks hinge on being timely, critical, and irreversible. The involvement of IoT in ransomware campaigns can amplify the impact of attacks because of cascading consequences especially in the case of critical infrastructure. In addition, IoT devices widen the attack surface through which ransomware can be deployed. These are conditions that can exacerbate disruptions.
Google Launches New Reward Program for Tsunami Security Scanner
Google says that the new, experimental program will give researchers patch rewards for creating plugins and application fingerprints. The former requires contributors to develop plugins that can be used for enhanced vulnerability detection, whereas the latter asks for web application modules that can be used to detect off-the-shelf web apps in an enterprise network.
Mac Users Targeted by Trojanized iTerm2 App
Earlier this month, it was reported that a search engine result for the keyword “iTerm2” led to a fake website called item2.net that mimics the legitimate iterm2.com. A fake version of the iTerm2 app, a macOS terminal emulator, can be downloaded from a link found in iterm2.net. When this app is executed, it downloads and runs g.py, a malicious Python script from 47[.]75[.]123[.]111. This malware, which Trend Micro has detected as TrojanSpy.Python.ZURU.A, collects private data from a victim’s machine.
4 Cybersecurity Strategies for Small and Midsize Businesses
Small and midsize businesses aren’t immune to cyber threats. They must research and prepare for attacks just as large enterprises would. Unfortunately, smaller companies typically have fewer resources and less talent available to help fortify against attacks. In this article, learn 4 cybersecurity strategies for small businesses.
Microsoft Warns of New Malware That Creates Secret Backdoor
Microsoft has recently discovered another type of malware, named FoggyWeb by Microsoft, that hackers are currently using to remotely steal network admin credentials. The credentials allow the attacker group, which the company has called Nobelium, to hack into admin accounts of the Active Directory Federation Services’ (AD FS) servers and control users’ access to various resources.
Telegram Bots Are Trying To Steal Your One-Time Passwords
While 2FA can improve upon the use of passwords alone to protect our accounts, threat actors were quick to develop methods to intercept OTP, such as through malware or social engineering. According to Intel 471, since June, a number of 2FA-circumventing services are abusing the Telegram messaging service.
What do you think about the new cyber bill that will mandate reporting on critical attacks? Share in the comments below or follow me on Twitter to continue the conversation: @JonLClay.
Read More HERE