This Week in Security News – July 23, 2021 VP, Threat Intelligence


Welcome to our weekly roundup, where we share what you need to know about cybersecurity news and events that happened over the past few days. This week, learn about StrongPity APT Group’s first Android malware. Also, read about the approval of STIX and TAXII cyberthreat sharing standards.
Read on:
StrongPity APT Group Deploys Android Malware for the First Time
Trend Micro recently investigated a malicious Android malware sample, which is believed can be attributed to the StrongPity APT group, that was posted on the Syrian e-Gov website. This is the first time the group has been publicly observed using malicious Android applications as part of its attacks.
Long-Awaited STIX, TAXII Cyberthreat Sharing Standards Approved
Open-source projects STIX and TAXII have been approved as full-fledged OASIS standards. The Structured Threat Information Expression (STIX) standard defines a language for sharing structured threat intelligence in a consistent, machine-readable manner to allow organizations to anticipate and respond to attacks faster and more effectively. Several top security companies including Trend Micro, IBM, and the U.S. Cybersecurity and Infrastructure Agency (CISA) already use it.
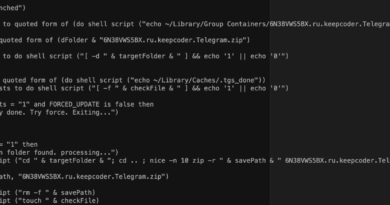
Updated XCSSET Malware Targets Telegram, Other Apps
The XCSSET campaign, which Trend Micro has continually monitored, has added more features to its toolset. Researchers have discovered the mechanism used to steal information from various apps, a behavior that has been present since XCSSET was first discussed.
Half of Organizations are Ineffective at Countering Phishing and Ransomware Threats
Half of US organizations are not effective at countering phishing and ransomware threats, Osterman Research reveals. The findings come from a study compiled from interviews with 130 cybersecurity professionals in mid-sized and large organizations. The study asked respondents to rate their effectiveness in 17 key best practice areas related to ransomware and phishing, ranging from protecting endpoints from malware infection to ensuring prompt patching of all systems.
Reduce Instances of Covid-19 Phishing Email Attacks
The Covid-19 pandemic has created an unlimited supply of news and topics for cybercriminals to utilize in their attacks, as well as major organizations to spoof. In this blog, learn what your organization can do to combat these timely threats.
How NIST is Changing Password Creation in 2021
To cope with the increasing number of cyber frauds and data thefts, the National Institute of Standards and Technology (NIST) has dispensed several guidelines that not only ensure security to the user but eventually help enterprises secure their crucial business information. These guidelines offer recommendations for users for creating strong passwords along with recommendations for vendors/verifiers that are handling passwords.
Prevent Cyber Risk as a Managed Service Provider (MSP)
IT Management software provider Kaseya was hit with a ransomware attack. As a result, the attack not only impacted the MSPs, but also the customers that they served. For an MSP, customer’s trust is crucial. You don’t want to be one of the 50 who got hit by a ransomware. For MSPs working with Trend Micro, there’s positive news. Trend Micro’s endpoint security provides an effective first line of defense against the Kaseya ransomware through predictive machine learning and behavior monitoring capabilities.
1,000 GB of Local Government Data Exposed by Massachusetts Software Company
A group of researchers found over 80 misconfigured Amazon S3 buckets holding data related to about 100 municipalities across the Northeast. The data ranged from residential records like deeds and tax information to business licenses and job applications for government positions. Due to the sensitive nature of the documents, many of the forms included people’s email address, physical address, phone number, driver’s license number, real estate tax information, and photos of property.
IoT Security Issues, Threats, and Defenses
The internet of things (IoT) has grown so broad that the development of its security had to quickly keep up. This blog discusses the basics of IoT security to help frame what it is, why it is necessary, and how it can be achieved.
CISA Details Malware Used in Attacks Targeting Pulse Secure Devices
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) released analysis reports for 13 malware samples discovered on Pulse Secure devices. In most cases, the malicious files are modified versions of Pulse Secure system applications. The attackers deployed webshells, trojans, credential harvesters, and utilities, enabling them to execute arbitrary commands on compromised systems, gain command and control (C&C) capabilities, hide their malicious activity, steal credentials, and read files on the system.
TeamTNT Activities Probed: Credential Theft, Cryptocurrency Mining, and More
TeamTNT, one of the most prolific and persistent malicious actor groups in recent memory, embarked on several campaigns in 2020 and early 2021. Most of these campaigns — although varying in tools, techniques, and scope — targeted cloud environments. A new report from Trend Micro sheds light on the tools and techniques used by TeamTNT and the potential impact of the group’s sundry malicious activities.
What are your thoughts on cybersecurity standards? Share in the comments below or follow me on Twitter to continue the conversation: @JonLClay.
Read More HERE