This Week in Security News – January 21, 2022


Read on:
Cybersecurity for Industrial Control Systems: Part 1
In this two-part series, Trend Micro looks at cybersecurity threats that affected industrial control systems endpoints and shares insights and recommendations to mitigate such threats. Trend Micro’s expert team extensively studied reported malware families in ICS endpoints to validate ICS security and establish a global baseline for examining threats that put these systems at risk.
CISA Urges US Orgs to Prepare for Data-Wiping Cyberattacks
Ukraine government agencies and corporate entities suffered coordinated cyberattacks last Friday where websites were defaced, and data-wiping malware was deployed to corrupt data and cause Windows devices to become inoperable. In response, the Cybersecurity and Infrastructure Security Agency (CISA) urges U.S. organizations to strengthen their cybersecurity defenses against data-wiping attacks.
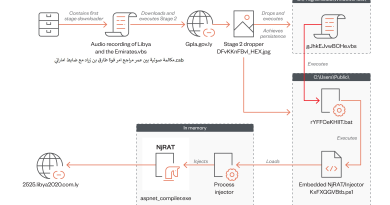
Earth Lusca Employs Sophisticated Infrastructure, Varied Tools and Techniques
This technical brief provides an in-depth look at Earth Lusca’s activities, the tools it employs in attacks, and the infrastructure it uses. Since mid-2021, Trend Micro has been investigating a rather elusive threat actor called Earth Lusca that targets organizations globally via a campaign that uses traditional social engineering techniques such as spear phishing and watering holes.
Crypto.Com Admits Over $30 Million Stolen by Hackers
Cryptocurrency exchange Crypto.com acknowledged that the company had lost well over $30 million in Bitcoin and Ethereum after a hack that took place on January 17th. The total value of the unauthorized withdrawals was 4,836.26 ETH and 443.93 BTC — equivalent to roughly $15.2 million and $18.6 million respectively, at current exchange rates — as well as $66,200 worth of other currencies. According to the post, 483 Crypto.com users had their accounts compromised.
New Ransomware Spotted: White Rabbit and Its Evasion Tactics
Trend Micro spotted the new ransomware family called White Rabbit, a newcomer that takes a page from Egregor, a more established ransomware family, in hiding its malicious activity and carries a potential connection to the advanced persistent threat (APT) group FIN8. In this blog, Trend Micro analyzes the ransomware family and brings into focus the familiar evasion tactics employed by this newcomer.
Ransomware Group REvil Dismantled in Raids, Russia Says
Russia’s main security agency said that at the request of the United States government, it has dismantled REvil, one of the most aggressive ransomware crime groups attacking Western targets, and arrested some of its members. The agency, known as the F.S.B., said “the organized crime gang ceased to exist” after a sweeping operation that was carried out in 25 locations across five Russian regions.
GitHub Action Runners: Analyzing the Environment and Security in Action
More organizations are applying a DevOps thought-process and methodology to optimize software development. One of the main tools used in this process is a continuous integration (CI) tool, which automates the integration of code changes from multiple developers working on the same project.
FBI & European Police Take Down Computer Servers Used in Major Cyberattacks Worldwide
The FBI and police from multiple European countries and Canada have taken down 15 computer servers that were used in “major international cyberattacks,” law enforcement agencies said. Europol, the European Union’s law enforcement agency, said that after seizing the servers, investigators have identified “more than 100 businesses” that were at risk of being hacked by cybercriminals, including ransomware groups.
Defending Users’ NAS Devices from Evolving Threats
To emphasize the importance of mitigating the risks of malware infection and targeted attacks on network-attached storage (NAS) devices, Trend Micro analyzed the technical details of two malware families that potentially included NAS devices in their existing business models, the REvil ransomware and StealthWorker botnets.
Biden to Expand National Security Agency Role in Government Cybersecurity
President Biden expanded the National Security Agency’s role in protecting the U.S. government’s most sensitive computer networks, issuing a directive intended to bolster cybersecurity within the Defense Department and intelligence agencies. The memorandum signed by President Biden mandates baseline cybersecurity practices and standards, such as two-factor authentication and use of encryption, for so-called national security systems.
Analyzing an Old Bug and Discovering CVE-2021-30995
A vulnerability found in 2021 has been patched and re-patched in the months since it was reported. In this blog, Trend Micro researchers analyze the bug and outline the process that led to the discovery of CVE-2021-30995.
Codex Exposed How Low Is Too Low When We Generate Code
In a series of blog posts, Trend Micro explores different aspects of Codex and assesses its capabilities with a focus on the security aspects that affect not only regular developers but also malicious users. This is the second part of the series.
What do you think about the latest cybercriminal crackdowns in Europe? Share in the comments below or follow me on Twitter to continue the conversation: @JonLClay.
Read More HERE