The Cybersecurity Measures CTOs Are Actually Implementing
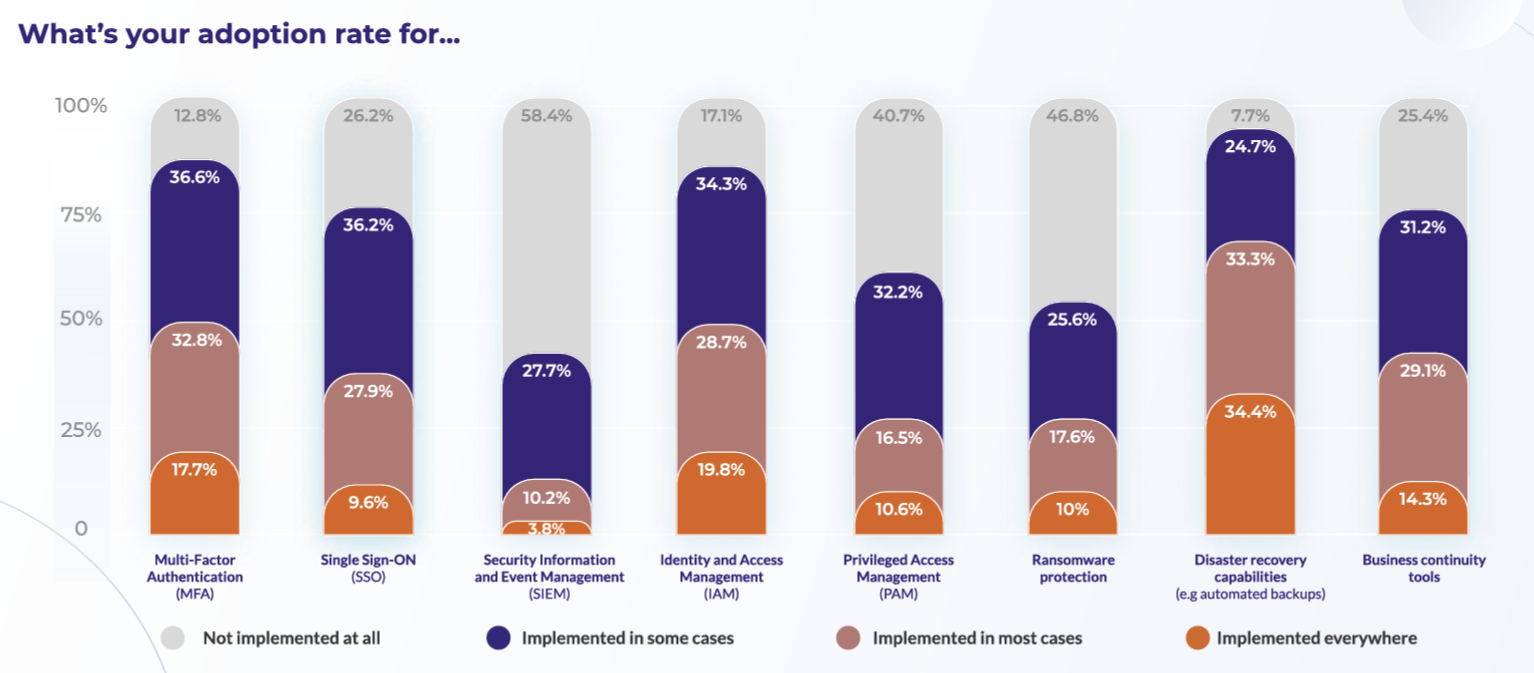
With cybersecurity top of mind for businesses, especially after the past year’s spectacular ransomware attacks, CTOs are taking a multipronged approach to protecting their company. A little over 87% of respondents to STX Next’s 2021 Global CTO Survey, which surveyed 500 global CTOs about the biggest challenges facing their organization, say they have implemented multifactor authentication (MFA) within their organization, and almost 83% say the same for identity and access management. Single sign-on (SSO) is also popular, adopted by about 74%. These findings jibe with Dark Reading’s 2021 Strategic Security Survey, in which 69% of respondents said that MFA was an effective cybersecurity measure.
What is surprising is that nearly half (46.8%) of CTOs admit their company has no specific ransomware protection at all, and that only 10% claim to implement ransomware guardrails everywhere. Only security information and event management was more overlooked, with less than 4% implementing it everywhere and almost 60% not using the monitoring and analysis technique at all.
Privileged access management (PAM) combines techniques including MFA and SSO to create extra security around accounts that require powerful permissions, because if such accounts are compromised, the intruder can gain unfettered access to the network. It has similar adoption numbers as ransomware protections: Only about 10% of respondents implement PAM everywhere, and about 17% use PAM in most cases. But only 40% admit to not using PAM at all.
The data suggests organizations rely on post-attack recovery instead of engaging in more aggressive preventatives: 92% of companies have at least some disaster recovery capabilities, in the form of automated backups, with over 34% saying they have universal backups. Business continuity tools are also popular, with about 75% of companies implementing them in at least some places.
Download the report from STX Next.
Read More HERE
