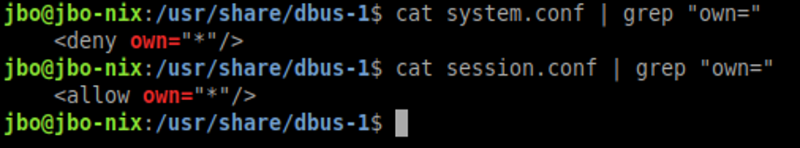
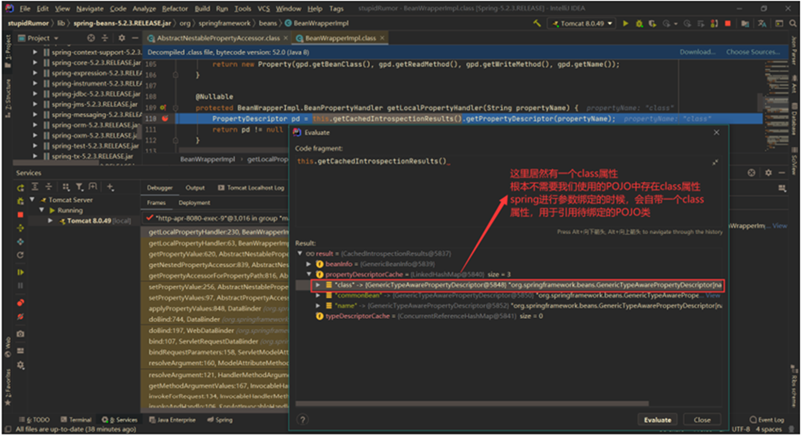
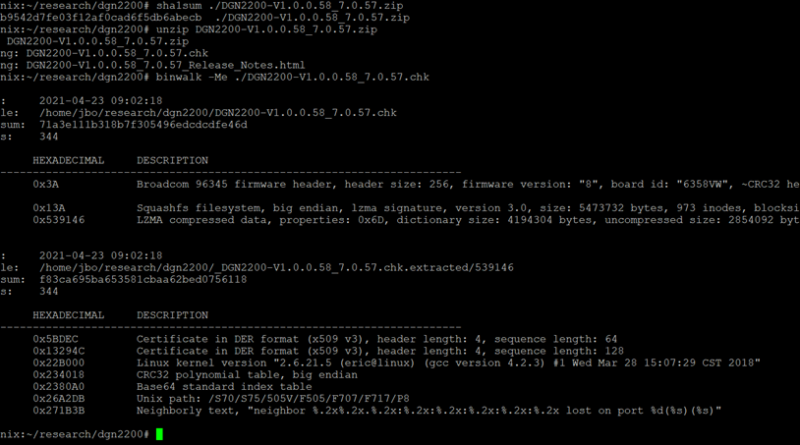
Microsoft has discovered several vulnerabilities, collectively referred to as Nimbuspwn, that could be chained together, allowing an attacker to elevate privileges to root on many Linux desktop endpoints. Leveraging Nimbuspwn as a vector for root access could allow attackers to achieve greater impact on vulnerable devices by deploying payloads and performing other malicious actions via arbitrary root code execution.
The post Microsoft finds new elevation of privilege Linux vulnerability, Nimbuspwn appeared first on Microsoft Security Blog. READ MORE HERE…
Read More