Bruised but Not Broken: The Resurgence of the Emotet Botnet Malware
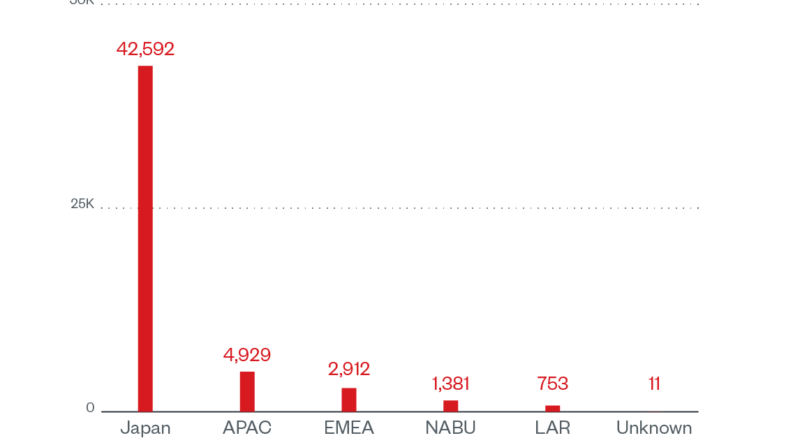
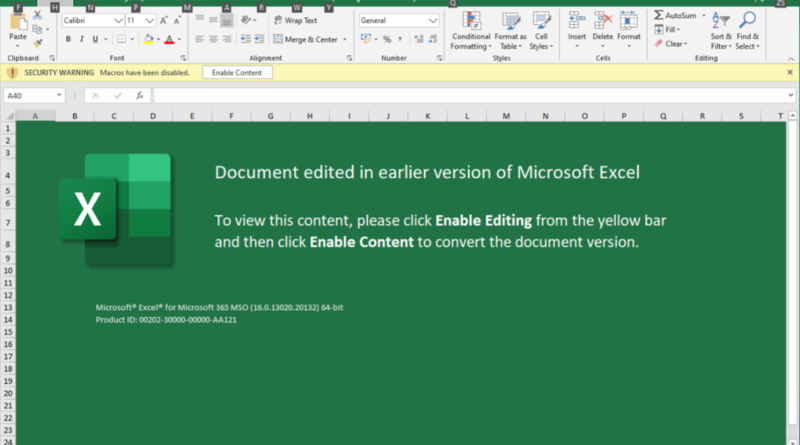
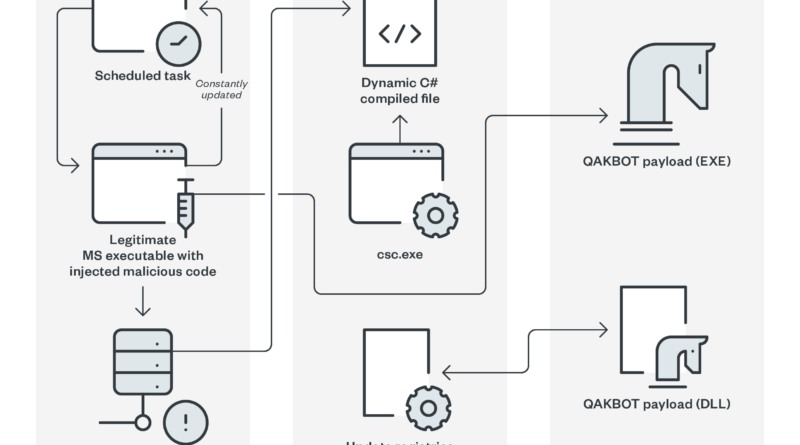
During the first quarter of 2022, we discovered a significant number of infections using multiple new Emotet variants that employed both old and new techniques to trick their intended victims into accessing malicious links and enabling macro content. Read More HERE…