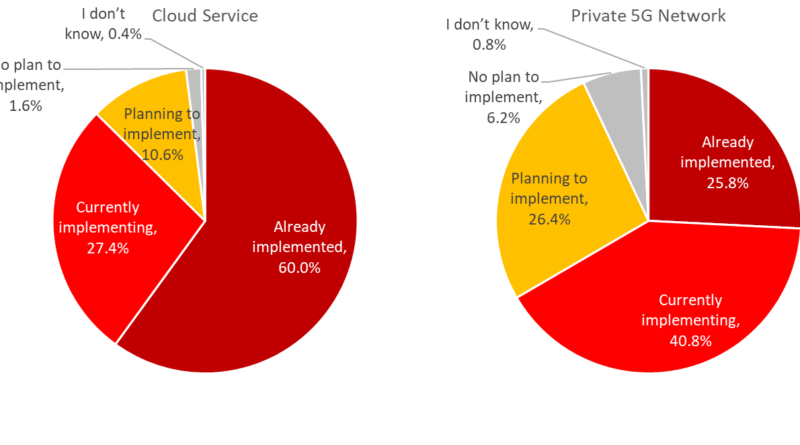
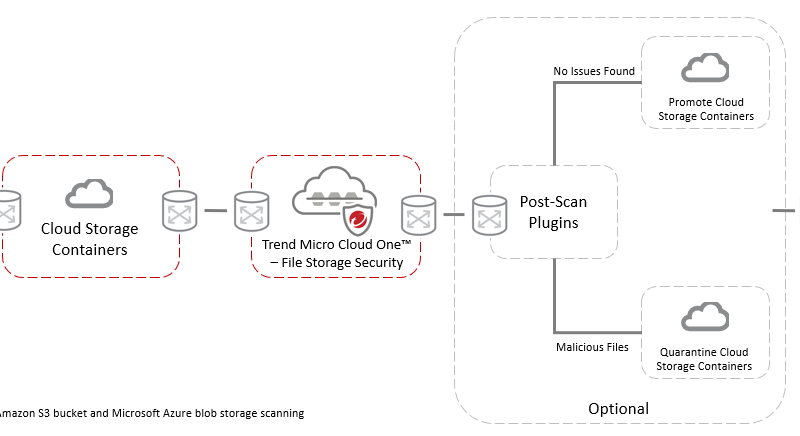
Secure Manufacturing on Cloud, Edge and 5G (Download PDF) Security Expert
This e-book provides you with insight into system changes brought on by factory production processes and explains how the cloud and 5G have transformed smart factories. You’ll also receive a look into how we map the attack scenario so you can identify the type of risks that lie throughout the entire system. Read More HERE…