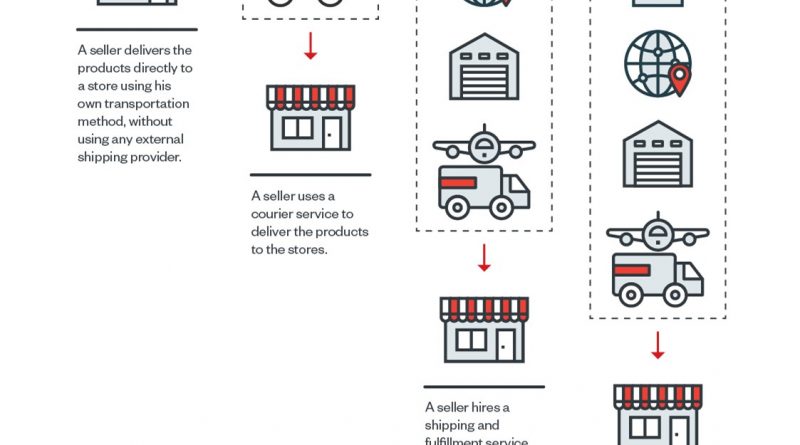
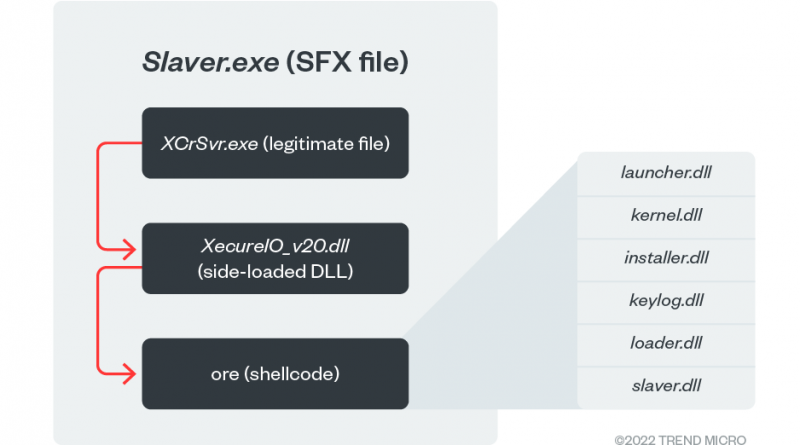
Security Risks in Logistics APIs Used by E-Commerce Platforms
Our research examines the security flaws that we found in the logistics API implementation of e-commerce platforms that can potentially expose the consumers’ personal information. We discuss the security risks that such flaws present for software engineers, e-commerce platform providers, and consumers. Read More HERE…