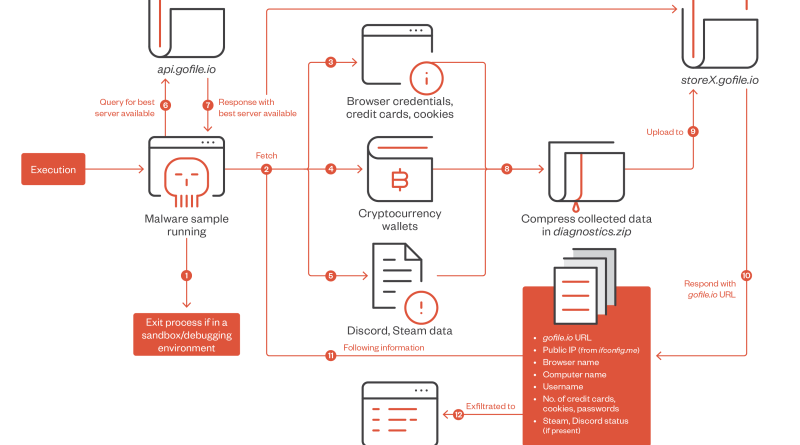
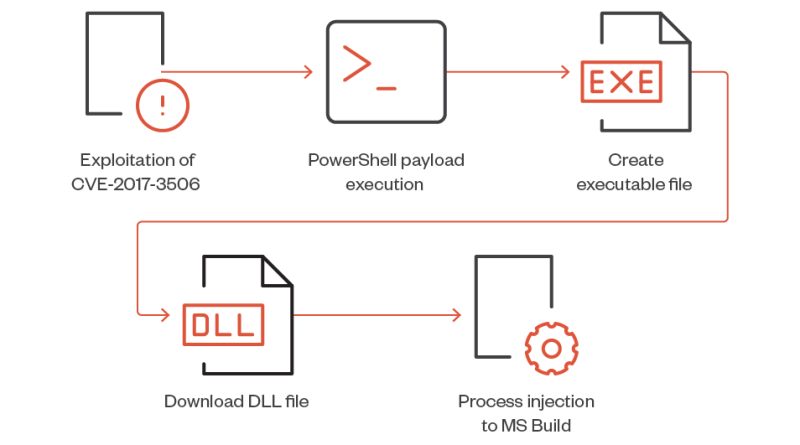
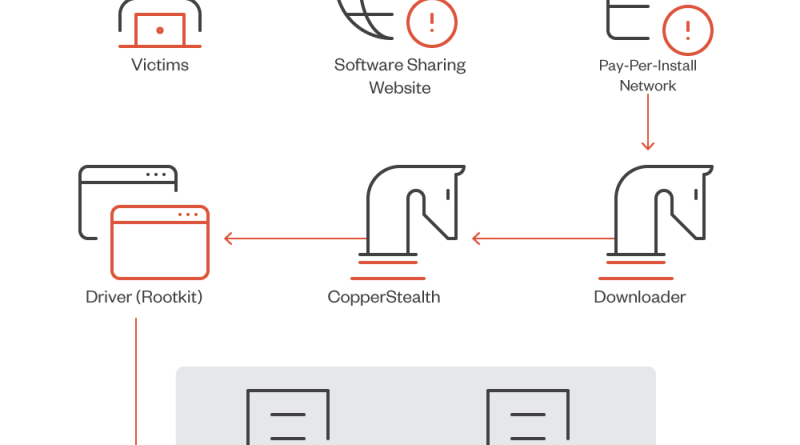
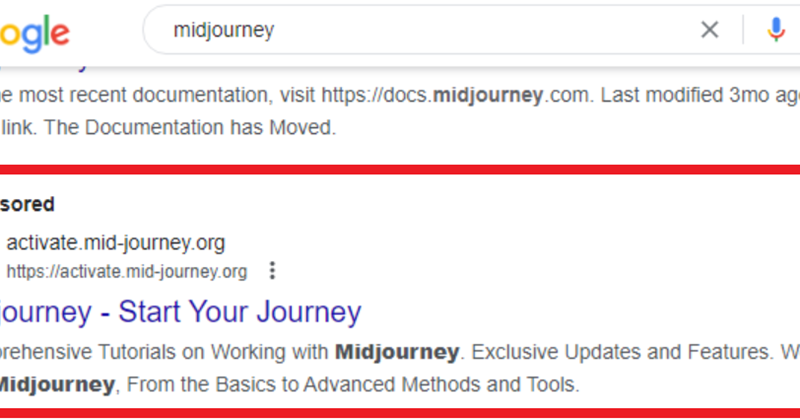
Rust-Based Info Stealers Abuse GitHub Codespaces
This is the first part of our security analysis of an information stealer targeting GitHub Codespaces (CS) that discusses how attackers can abuse these cloud services for a variety of malicious activities. Read More HERE…