Trend Micro Research : Cloud
Attacking The Supply Chain: Developer
In this proof of concept, we look into one of several attack vectors that can be abused to attack the supply chain: targeting the developer. With a focus on the local integrated developer environment (IDE), this proof considers the execution of malicious build scripts via injecting commands when the project or build is incorrectly “trusted”. Read More HERE…
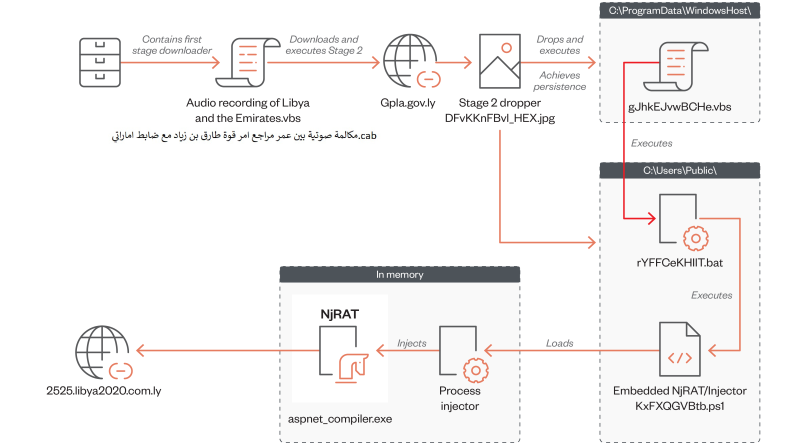
Earth Bogle: Campaigns Target the Middle East with Geopolitical Lures
We discovered an active campaign ongoing since at least mid-2022 which uses Middle Eastern geopolitical-themed lures to distribute NjRAT (also known as Bladabindi) to infect victims across the Middle East and North Africa. Read More HERE…
Abusing a GitHub Codespaces Feature For Malware Delivery
Proof of Concept (POC): We investigate one of the GitHub Codespaces’ real-time code development and collaboration features that attackers can abuse for cloud-based trusted malware delivery. Once exploited, malicious actors can abuse legitimate GitHub accounts to create a malware file server. Read More HERE…
What is Red Teaming & How it Benefits Orgs
Running real-world attack simulations can help improve organizations’ cybersecurity resilience Read More HERE…
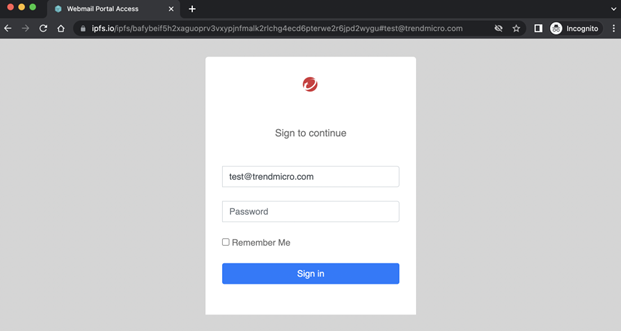
Web3 IPFS Only Used for Phishing – So Far
We discuss the use of the InterPlanetary File System (IPFS) in phishing attacks. Read More HERE…