Protecting S3 from Malware: The Cold Hard Truth

Cloud object storage is a core component of any modern application. When files move through your applications, it’s critical to protect your systems and users from malicious files.
Trend Micro has provided cloud-native, scalable file protection for our customers since 2020. We’re now starting to see other vendors try to catch up by bringing similar capabilities to the market, but frankly I’m underwhelmed with their offerings.
I love the cloud security space because there is so much new technology, which enables interesting solutions. Our customers are constantly pushing us to support the innovative use cases they are bringing to market. I can forgive new entrants to this space for not supporting every scenario, but there are some non-negotiable requirements for effective malware protection in the cloud:
Requirements for Effective File Storage Security
1. You need to actually support the files you’re using
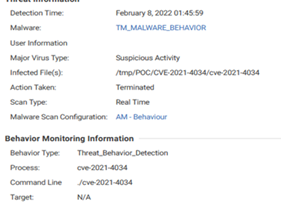
Amazon S3 supports objects up to 5 terabytes. When I look at other offerings, like Prisma Cloud Data Security, their limit is 100 MB for malware scanning, and only limited file types[1]. How is that acceptable?
Trend Micro Cloud One supports some of the largest media companies on the planet, scanning enormous files in the cloud – any type and any size.
2. Don’t lose control of the files being scanned
Cloud builders go to great lengths to manage the sovereignty and security of data. When I see malware scanning solutions like CrowdStrike Falcon S3 Bucket Protection that send your files to an endpoint outside of your control, I shudder thinking of the compliance and data security problems that raises.
That’s why Cloud One – File Storage Security doesn’t send files outside of your account. All scanning is performed inside your cloud environment, under your control. The way it should be.
3. Scale with the Cloud
We all use the cloud for the great benefits of elasticity and scalability to handle peaks of traffic automatically. Make sure your malware scanning does the same thing! It feels so old fashioned when customers deploy something like ClamAV on EC2 instances or SentinelOne’s Storage Sentinel for Amazon S3 that runs a scan engine on EC2. That EC2 instance is running all the time – even if files aren’t being scanned. And when there are a LOT of files that need to be scanned, scaling up EC2 scanners is slower and much more involved.
Instead, leveraging cloud native solutions aligns better to protecting cloud native storage, costs nothing when idle, they scale instantly, and can be used to scan many objects in parallel, with a scan that takes seconds, not minutes or hours.
4. Scale across clouds
Most companies these days don’t use just one cloud, they diversify with a multi-cloud environment. Palo Alto, CrowdStrike, SentinelOne – none support multi-cloud because they omit Microsoft Azure or Google Cloud Platform.
Cloud One – File Storage Security supports AWS, Azure, and GCP, which is critical for multi-cloud environments.
It’s not easy to create beautiful malware scanning in the cloud, but there are many examples of doing it wrong. If you don’t believe me, give it a try for yourself. You can get started with Trend Micro Cloud One for free right here.
Read More HERE