Microsoft to acquire RiskIQ to strengthen cybersecurity of digital transformation and hybrid work
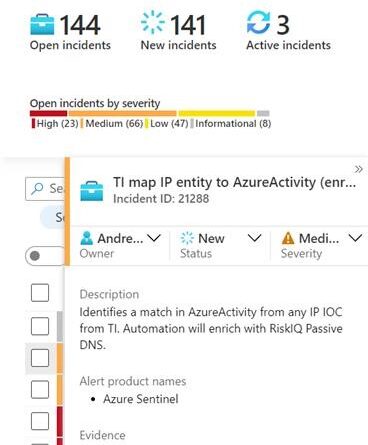
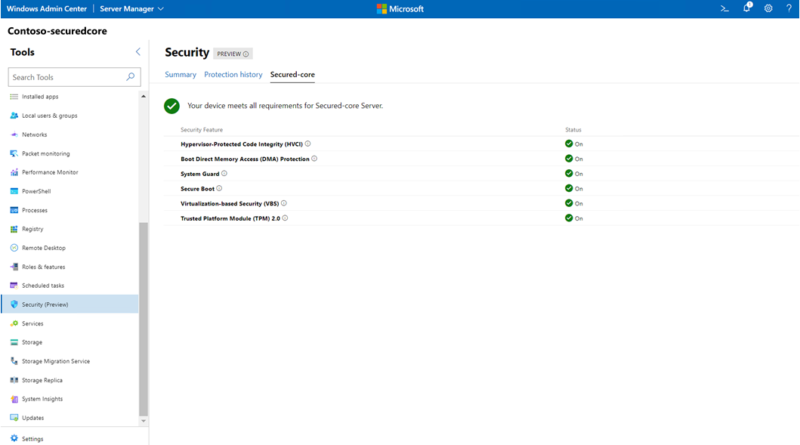
Microsoft is announcing that we have entered into a definitive agreement to acquire RiskIQ, a leader in global threat intelligence and attack surface management, to help our shared customers build a more comprehensive view of the global threats to their businesses, better understand vulnerable internet-facing assets, and build world-class threat intelligence.
The post Microsoft to acquire RiskIQ to strengthen cybersecurity of digital transformation and hybrid work appeared first on Microsoft Security Blog. READ MORE HERE…