New Russia-affiliated actor Void Blizzard targets critical sectors for espionage
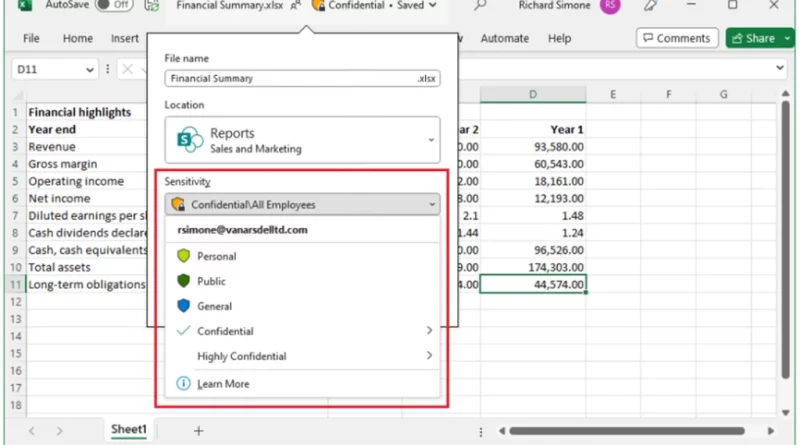
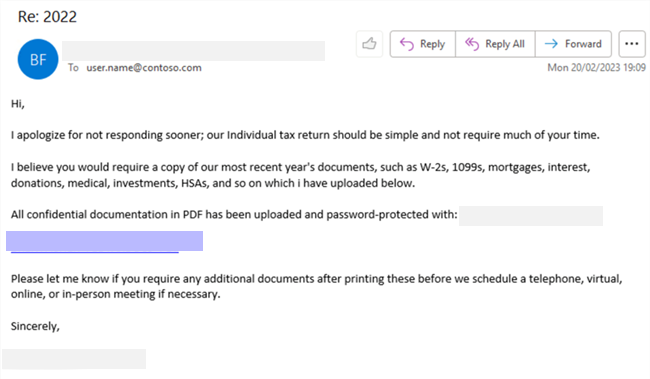
Microsoft Threat Intelligence has discovered a cluster of worldwide cloud abuse activity conducted by a threat actor we track as Void Blizzard, who we assess with high confidence is Russia-affiliated and has been active since at least April 2024. Void Blizzard’s cyberespionage operations tend to be highly targeted at specific organizations of interest to Russia, including in government, defense, transportation, media, non-governmental organizations (NGOs), and healthcare sectors primarily in Europe and North America.
The post New Russia-affiliated actor Void Blizzard targets critical sectors for espionage appeared first on Microsoft Security Blog. READ MORE HERE…