Franken-phish: TodayZoo built from other phishing kits
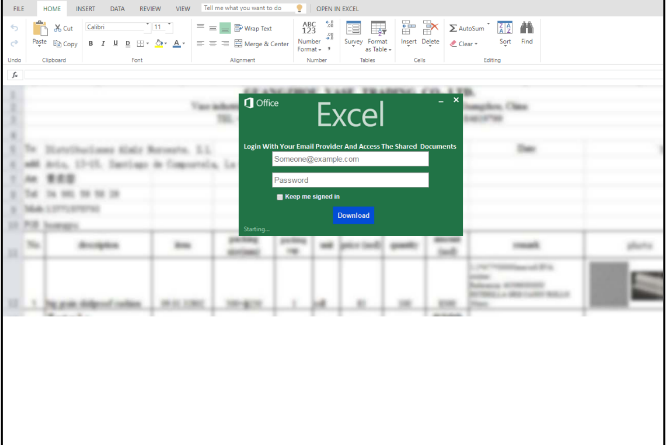
A phishing kit built using pieces of code copied from other kits, some available for sale through publicly accessible scam sellers or are reused and repackaged by other kit resellers, provides rich insight into the state of the economy that drives phishing and email threats today.
The post Franken-phish: TodayZoo built from other phishing kits appeared first on Microsoft Security Blog. READ MORE HERE…