FoggyWeb: Targeted NOBELIUM malware leads to persistent backdoor
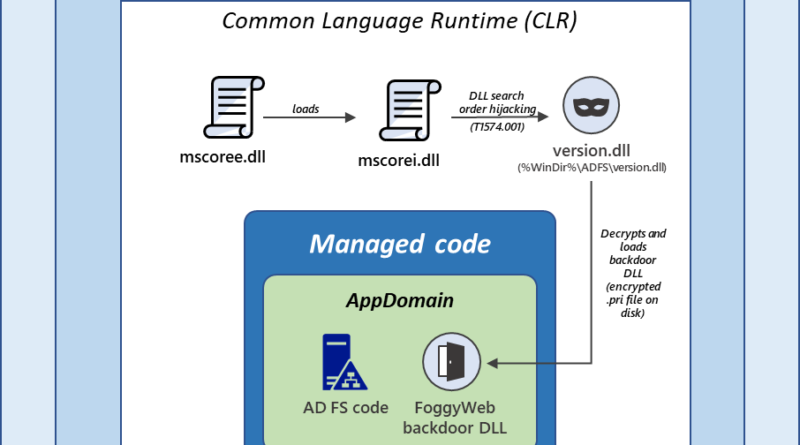
In-depth analysis of newly detected NOBELIUM malware: a post-exploitation backdoor that Microsoft Threat Intelligence Center (MSTIC) refers to as FoggyWeb. NOBELIUM uses FoggyWeb to remotely exfiltrate the configuration database of compromised AD FS servers, decrypted token-signing certificate, and token-decryption certificate, as well as to download and execute additional components.
The post FoggyWeb: Targeted NOBELIUM malware leads to persistent backdoor appeared first on Microsoft Security Blog. READ MORE HERE…