In hot pursuit of ‘cryware’: Defending hot wallets from attacks
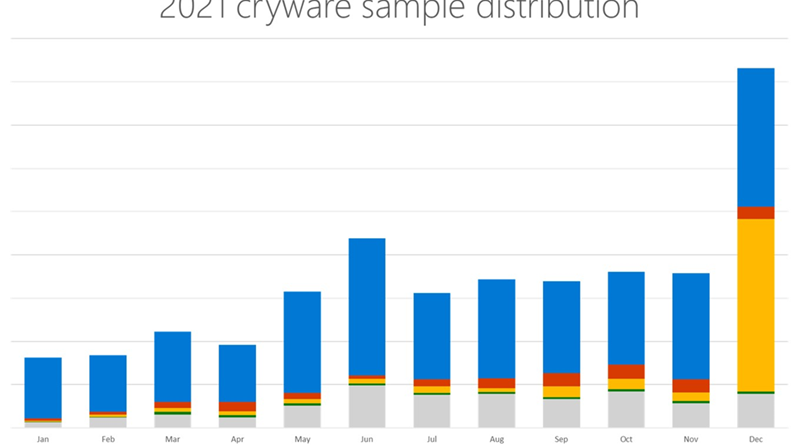
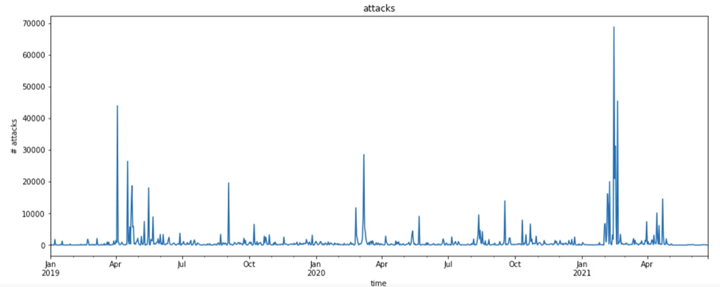
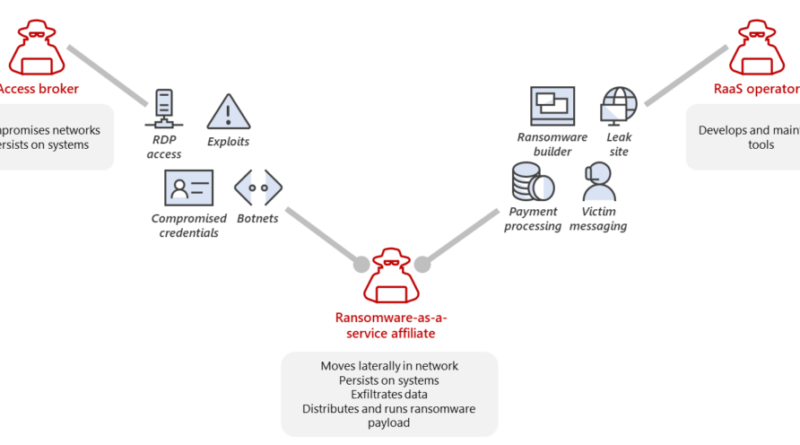
The rise in cryptocurrency market capitalization paved the way to the emergence of threats Microsoft security researchers are referring to as “cryware”—information stealers focused on gathering and exfiltrating data from non-custodial cryptocurrency wallets.
The post In hot pursuit of ‘cryware’: Defending hot wallets from attacks appeared first on Microsoft Security Blog. READ MORE HERE…