Microsoft security experts outline next steps after compromise recovery

Who is CRSP?
The Microsoft Compromise Recovery Security Practice (CRSP) is a worldwide team of cybersecurity experts operating in most countries, across both public and private organizations, with deep expertise to secure an environment post-security breach and to help you prevent a breach in the first place. As a specialist team within the wider Microsoft cybersecurity functions, we predominantly focus on reactive security projects for our customers. The main types of projects we undertake are:
- Compromise recovery: Giving customers back control of their environment after a compromise.
- Rapid ransomware recovery: Restore business-critical applications and limit ransomware impact.
- Advanced threat hunting: Proactively hunt for the presence of advanced threat actors within an environment.
How to update your security processes
Friday afternoon. It is always a Friday afternoon. The phone rings and yet another organization has suffered a total breakdown of IT with everything from data loss to ransomware. The CRSP team does contracting and off we go to start working. Sometimes we work magic, sometimes we are lucky, and sometimes it is just very hard work, and in the end, we get to a stable and secured environment. But what happens with the organization afterward?
A compromise recovery, in general, means that we are force a number of security changes that should have been implemented during the last years, in normally six weeks. It is intense, and it changes how administrators work and how systems break. The main goals are to take back control, keep that control, and add this mindset to the customer.
We have seen many cases of inattentive operational procedures just because they are easy, they work due to dependencies on a legacy app, and they are cheap, but all of them inevitably open up for an attacker to exploit the systems. In a rather recent case, the lowest bidder got the management of an IT environment and gave all their support engineers Domain Admin access that they used for signing in everywhere. So when an employee accidentally clicked on an email attachment, the attacker got instant Domain Admin access and the takeover was quickly executed. A few hours after the click, the environment was encrypted.
Even if we make many technical changes, the important ones are new processes and procedures when administrating the environment. The tier model, privilege access workstations, and similar tools are part of the delivery, but also strict procedures on how new machines are deployed, how administrator accounts are to be used, and how it all should be monitored.
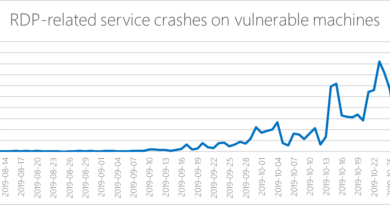
Monitoring is a big game-changer for many customers. Yes, they might have a security information and event management (SIEM) system today, and they might have a security operations center (SOC) that collects information from the environment but, alas, without the proper procedures, configuration, and speed, they are struggling to keep up with an active attacker. When we deploy our tools, we are also pushing monitoring on top of them, and we start to train our customers on how to properly use monitoring, AI, and machine learning, as well as what to look for and how they can start to automate the responses.
When we close off the project, our customers have not only gotten an upgraded administrative environment, but also a set of new processes to follow that might feel challenging in the beginning. It is seldom, however, that the staff that has to follow those processes complain. Part of the delivery is education on what the attackers did to take over the environment, and with this training comes the insight that everything that is cumbersome and challenging for an administrator with the right tools is close to impossible for a hacker; things like privilege access workstations, multifactor authentication, and monitoring identities all have their place.
Following Microsoft Security processes that have been tested over and over, we achieve a successful recovery together with our customers and have helped them to embark on a new journey towards a more secure environment.
Learn more
Other blogs from the CRSP:
To learn more about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us at @MSFTSecurity for the latest news and updates on cybersecurity.
READ MORE HERE