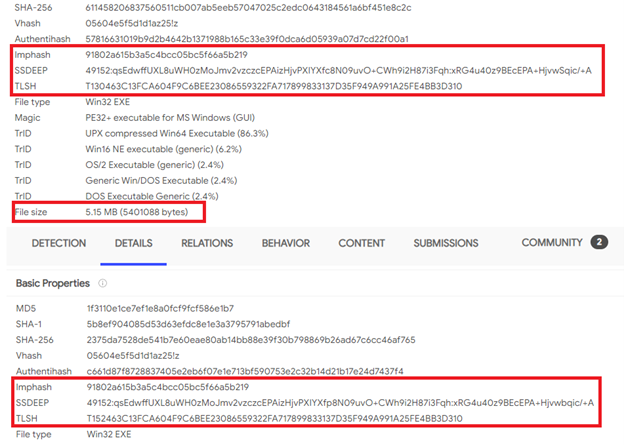
Enterprises can look for more transparency from software vendors after the Biden Administration’s recent mandate that software bills of materials be provided by companies attempting to do business with the federal government.Software bills of materials, frequently abbreviated to SBOMs, aren’t a new concept. The idea comes from the manufacturing sector, where it’s often crucial for buyers to fully understand the components and materials that were used to make a particular piece of equipment.The 10 most powerful companies in enterprise networking 2021
For example, a train engine might contain parts that aren’t rated for certain levels of vibration stress, making it unsuitable for use on a particular type of track. The goal of an SBOM is similar, listing all the proprietary, open source, and licensed components being used in a particular piece of software, so that a buyer can review it and check whether any of those components are outdated or insecure.To read this article in full, please click here READ MORE HERE…
Read More