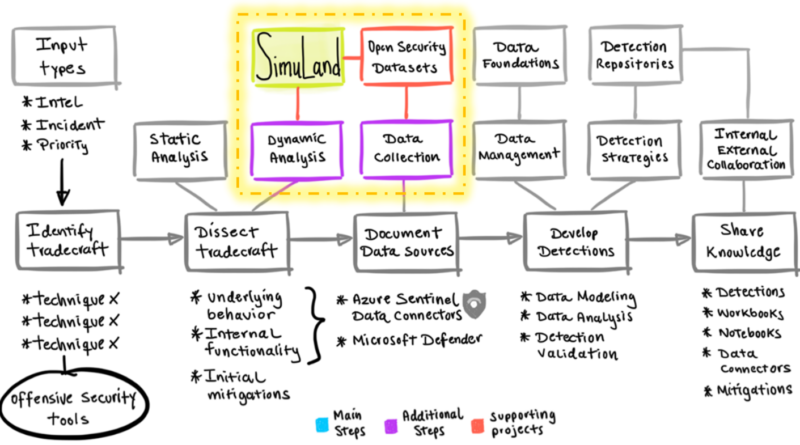
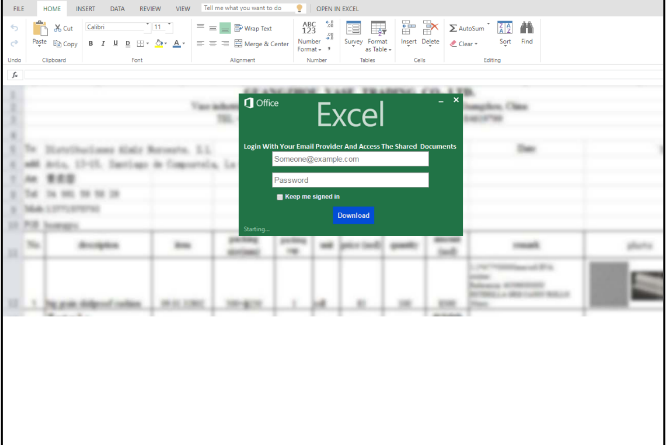
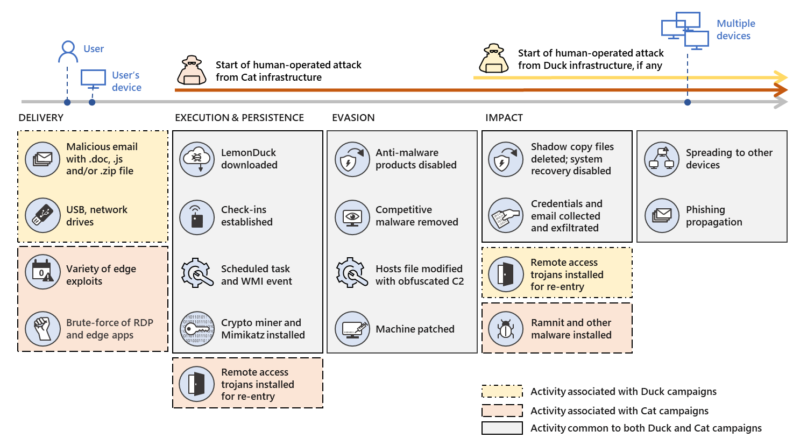
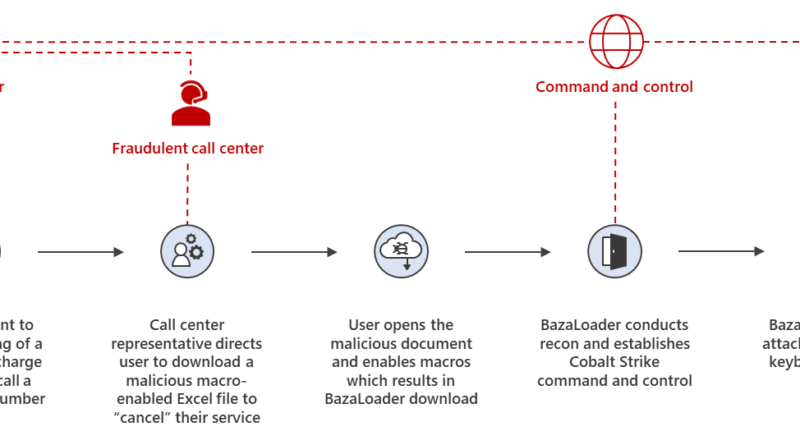
7 ways to harden your environment against compromise
Here at the global Microsoft Compromise Recovery Security Practice (CRSP), we work with customers who have experienced disruptive security incidents to restore trust in identity systems and remove adversary control. During 2020, the team responded to many incidents involving ransomware and the deployment of crypto-mining tools.
The post 7 ways to harden your environment against compromise appeared first on Microsoft Security Blog. READ MORE HERE…