Dismantling ZLoader: How malicious ads led to disabled security tools and ransomware
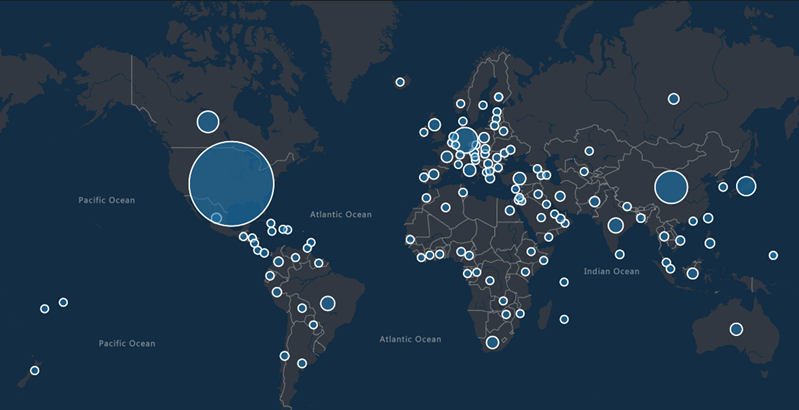
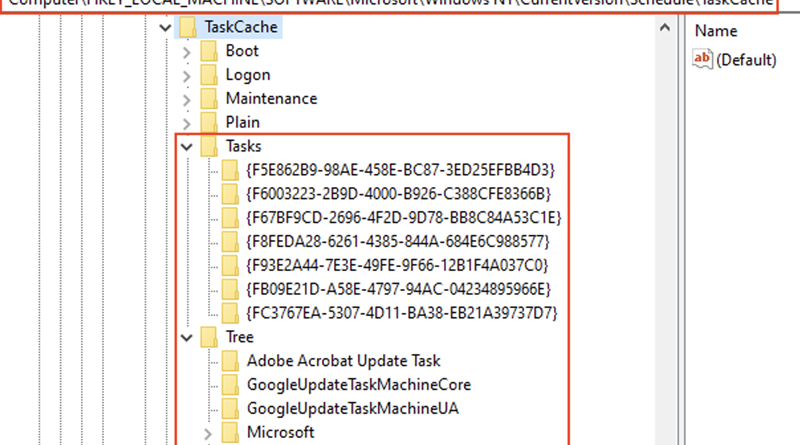
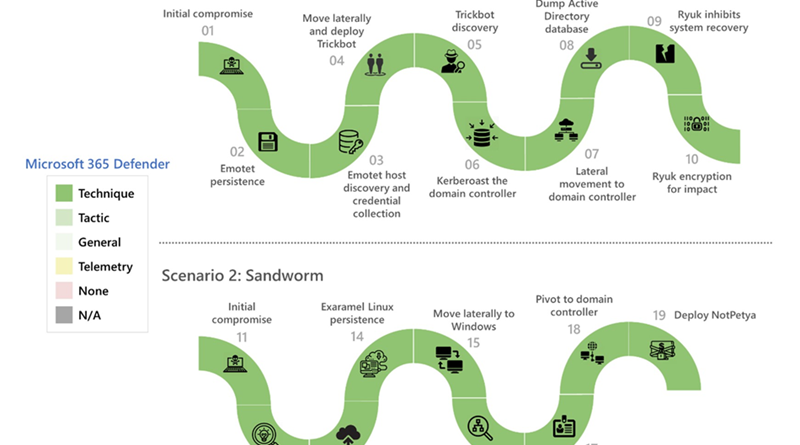
Microsoft took action against the ZLoader trojan by working with telecommunications providers around the world to disrupt key ZLoader infrastructure. In this blog, we detail the various characteristics for identifying ZLoader activity, including its associated tactics, recent campaigns, and affiliated payloads, such as ransomware.
The post Dismantling ZLoader: How malicious ads led to disabled security tools and ransomware appeared first on Microsoft Security Blog. READ MORE HERE…