Business email compromise campaign targets wide range of orgs with gift card scam
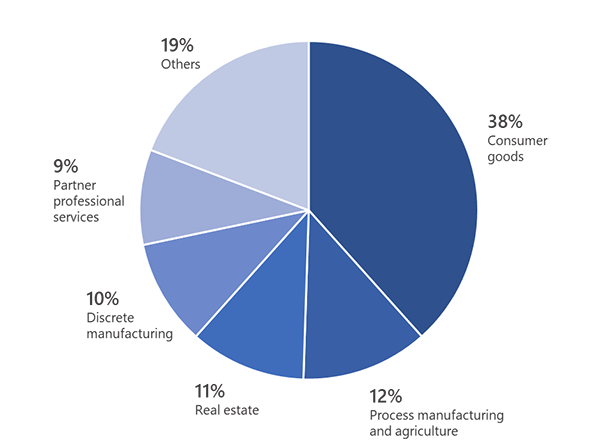
Read our investigation of a BEC campaign that used attacker-created email infrastructure to facilitate gift card theft targeting the consumer goods, process manufacturing and agriculture, real estate, discrete manufacturing, and professional services sectors.
The post Business email compromise campaign targets wide range of orgs with gift card scam appeared first on Microsoft Security. READ MORE HERE…