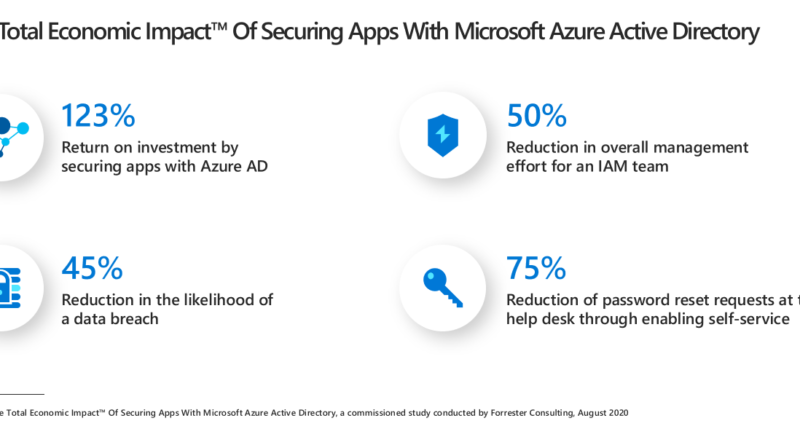
New Forrester study shows customers who deploy Microsoft Azure AD benefit from 123% ROI.
Results from a Forrester TEI study show that customers who secure apps with Microsoft Azure Active Directory can improve user productivity, reduce costs, and gain IT efficiencies to generate a 123 percent ROI.
The post New Forrester study shows customers who deploy Microsoft Azure AD benefit from 123% ROI. appeared first on Microsoft Security. READ MORE HERE…