SVB collapse’s mix of money, urgency and uncertainty makes it irresistible to scammers
The collapse of Silicon Valley Bank (SVB) late last week sent tremors through the global financial system, creating opportunities for short-sellers – and numerous species of scammer.
According to various researchers and security firms, threat actors are already out hunting for SVB-exposed prey through both passive and active phishing scams, including similar fake domains and business email compromise (BEC) attacks.
Johannes Ullrich, dean of research at SANS Technology Institute, clocked a rapid increase in the number of domain registrations containing the term “SVB” since the March 10 collapse.
“Over the weekend, we saw a number of domain registrations tracking the Silicon Valley Bank failure (for example svblogin.com, loginsvg.com and such),” he wrote on LinkedIn.
“We also got reports that former SVB customers are sending simple emails to update their vendors with new ACH [automated clearing house] account information. Please stop that. Just a matter of time for the bad guys to spoof emails like that (if they don’t already do it).”
Ullrich also noted that SVB’s failure has some attractive features for scam operators: money, urgency and uncertainty.
“For many, it isn’t clear how to communicate with SVB, what website to use, or what emails to expect (or where they will come from)” wrote Ullrich.
Ullrich isn’t the only one noticing an increase in SVB-referencing domain registrations.
New domain registrations relating to Silicon Valley Bank are emerging. Some could be #phishing campaigns. Listed below is what we’re seeing now. Keep in mind not all are scammy, and not all scammy domains targeting SVB will have SVB-related terms: https://t.co/mHjfZQIQAf pic.twitter.com/Au7AbA0GhX
— SecuritySnacks (@SecuritySnacks) March 13, 2023
The infrastructure leveraging the domains has also started to appear.
Expect different threat actors to exploit the current situation with SVB. Started to see some infrastructure being setup that could be used for phishing / scams. login-svb[.]com cash4svb[.]com svbclaim[.]com svbdebt[.]com pic.twitter.com/rn9ltBsxDU
— Jaime Blasco (@jaimeblascob) March 12, 2023
Cloudflare said on Tuesday it had detected a large Know-Your-Customer (KYC) phishing campaign that leaned on SVB branding in a DocuSign themed template. The web security firm said that within hours of the campaign, it had detected its use 79 times.
An attack sent to the company’s CEO included HTML code with an initial link that redirected four times, eventually landing on an attacker-controlled docusigning[.]kirklandellis[.]net website.
“The included HTML file in the attack sends the user to a WordPress instance that has recursive redirection capability. As of this writing, we are not sure if this specific WordPress installation has been compromised or a plugin was installed to open this redirect location,” said Cloudflare.
Among the cyber guardian’s recommendations is a suggestion to encourage end user vigilance on messages relating to ACH or SWIFT.
“Given its large scale prevalence, ACH & SWIFT phish are frequent tactics leveraged by threat actors to redirect payments to themselves,” said Cloudflare. It said it hadn’t yet seen any large scale ACH campaigns utilizing the SVB brand – but that doesn’t mean such schemes aren’t imminent.
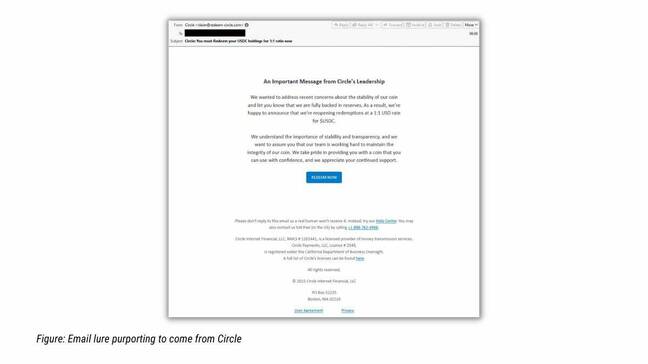
American cyber security firm Proofpoint said on Tuesday its researchers had tracked “a campaign leveraging lures related to USD Coin (USDC), a digital stablecoin tied to USD that was impacted by the SVB collapse.”
Malicious SendGrid accounts sent messages impersonating cryptocurrency brands and asked victims to claim their crypto through URLs that were redirected.
“Clicking the button would try to open a DeFi URL, so the victim would need to have a DeFi handler installed, such as MetaMask wallet. The victim would then be lured to install a Smart Contract that would transfer the contents of the victim’s wallet to the attacker,” said Proofpoint.
According to the firm, once Circle – the company which issues USD Coin (USDC) – announced it had cash reserves in SVB, the threat actor started spoofing the fintech with a lure promising 1:1 USDC to USD redemption.
“Proofpoint recommends that anyone involved in handling financial info or transactions exercise additional caution and diligence as messages could emanate from fraudsters,” tweeted the firm. ®
READ MORE HERE