Surface expands its Secured-core portfolio with the new Surface Laptop 4 powered by AMD Ryzen™ Mobile Processors

As operating systems are becoming more secure and resistant to compromise, advanced vectors like firmware, kernel and hardware direct memory access (DMA) have emerged as new favored targets for threat actors. Recent trends indicate a substantial growth in the number of hardware and firmware exploits. The March 2021 Security Signals report, commissioned by Microsoft, indicates that a vast majority of enterprise customers have experienced at least one firmware attack in the past two years.
To safeguard against increasingly sophisticated and targeted attacks, we need more than just software protection – integrated hardware and software security is now essential in an era of heightened threat. Collaborating closely with AMD, Microsoft is proud to announce our latest Secured-core offering, the all-new Surface Laptop 4 powered by AMD Ryzen™ Mobile Processors. These devices offer comprehensive security out of the box with tightly integrated hardware, software, firmware, and identity protection layers.
Defense against hardware and firmware exploits
Leveraging hardware for security
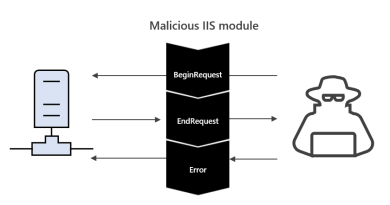
At the heart of the Surface Laptop 4, the device leverages the Trusted Platform Module 2.0 (TPM) and the AMD Ryzen™ Mobile Processors with System Guard to boot securely and minimize the impact of firmware vulnerabilities by sandboxing firmware to protect critical subsystems and sensitive data. Kernel Direct Memory Access Protection is pre-enabled on these devices, helping to ensure that the system is protected against malicious and unintended Direct Memory Access (DMA) attacks for all DMA-capable devices, such as PCI devices, thwarting the entire class of drive-by DMA attacks like Thunderspy.
The TPM 2.0 serves as the hardware root-of-trust for the Surface Laptop 4. With hardware protections for sensitive assets like BitLocker keys and security measurements for the state of the system, the TPM 2.0 helps make the Surface Laptop 4 ready for Zero Trust security.
UEFI firmware protection
As pointed out in the Security Signals report, firmware is emerging as a primary target because it’s where devices store sensitive information, like credentials and encryption keys. To address this Microsoft introduced its own open-source UEFI to help enable a secure and maintainable interface to manage firmware. On the Surface side, we have been enabling the automation of firmware protection since the 2015 release of Surface Pro 4. That’s when we made the decision to build our own Microsoft UEFI 1 and facilitate full transparency for our customers with the open-source project called Project Mu.
If you’re not already familiar with UEFI, it stands for Unified Extensible Firmware Interface. It’s essentially a modern version of a BIOS that initializes and validates system hardware components, boots Windows 10 from an SSD, and provides an interface for the OS to interact with the keyboard, display, and other input/output devices.
Centralized device management down to the firmware level
As Microsoft further developed the UEFI for Surface, we also built tools for managing and updating UEFI, beginning with SEMM (Surface Enterprise Management Mode). You can use it as a stand-alone tool or integrated with Microsoft Endpoint Configuration Manager to manage the UEFI settings on your Surface. SEMM lets you remotely enable and disable key components of Surface devices that would otherwise require you to physically go to every machine and boot straight into the UEFI (Power button + Volume Up). From a security perspective this is important as the more components you disable, that are not normally used, the smaller the attack vector.
Aligned to Microsoft’s broader commitments, we moved SEMM capabilities to the cloud with the launch of DFCI (Device Firmware Configuration Interface). DFCI enables cloud-based control over UEFI settings through the Intune component of Microsoft Endpoint Manager. The best part is that DFCI can be enabled via policy and deployed with Windows Autopilot before anyone even logs into the device. With DFCI a Surface device can be fully managed from Windows 10 down to firmware all through the power of the cloud and Microsoft Endpoint Manager.
Surface drives innovation into firmware security
Surface takes a multi-pronged approach to raise the security of our UEFI. To start, it can be updated via Windows Update. Our UEFI does not require an outside tool from a third party or download site. In fact, when the vulnerability of Spectre and Meltdown was announced, Surface already had a fix available that was automatically pushed to every Surface device accepting updates. Windows Update patched the microcode of our processors all through UEFI. Another security step we take is to lock down the UEFI, to help protect against known exploits. Surface UEFI uses a combination of Platform Secure Boot (PSB) and UEFI Secure Boot, which translates to a measured and signed firmware check at each stage in the initial boot process.
Proactive operating system protection
Along with limiting to a small, trusted computing base by establishing a hardware root of trust, Surface Laptop 4 confirms that code running within that trusted computing base runs with integrity.
Virtualization-based security (VBS) isolates the operating system and provides a hardware-based security boundary, thereby separating security features and sensitive code and data from vulnerabilities in the operating system. Hypervisor-enforced Code Integrity (HVCI) checks the system software before it is loaded, allowing only executables that are signed by known, approved authorities to start. The hypervisor also helps ensure that kernel executable memory is not writable. This prevents the modifications of sensitive kernel structures and provides strong protections against kernel viruses and malware. Time and again, the protections offered by VBS and HVCI have been shown to provide essential resistance against practical real-world threats.
Identity protection
Complementing the platform security provided by secured-core and Project Mu, Surface Laptop 4 helps ensure that user identities and credentials are protected against theft, compromise, and phishing attacks.
Windows Hello helps prevent phishing and credential-based attacks through a combination of biometric sensors and hardware-based credential storage. Using your face, secure FIDO2 key, or PIN, Windows Hello allows you to sign in password-free and gives you a faster, more secure way to unlock your device.
Windows Defender Credential Guard, an optional feature that can be enabled, leverages VBS to help isolate secrets and confidential information such that only privileged system software can access it. This helps prevent identity attack techniques such as Pass-the-Hash and Pass-the-Ticket.
New Surface expands Secured-core PC line
Surface Laptop 4, powered by AMD Ryzen™ Mobile Processors, joins Surface Pro X as the second secured-core PC offering in the Surface portfolio. These devices provide powerhouse protection out of the box, with capabilities such as Virtualization-Based Security, System Guard, and Kernel DMA protection enabled by default. With these devices, users and businesses can be confident that they have the right protections in place to mitigate security risks and simplify the end-user experience in configuring the device.
Find out more about our Secured-core PC lineup.
1 Surface Go and Surface Go 2 use a third-party UEFI and do not support DFCI. DFCI is currently available for Surface Laptop Go, Surface Book 3, Surface Laptop 3, Surface Pro 7, Surface Pro 7+ and Surface Pro X. Find out more about managing Surface UEFI settings at https://docs.microsoft.com/surface/manage-surface-uefi-settings.
READ MORE HERE