Sony Investigating After Hackers Offer To Sell Stolen Data
Sony has launched an investigation after a cybercrime group claimed to have compromised the company’s systems, offering to sell stolen data.
A representative of the Japanese electronics and entertainment giant told SecurityWeek that it’s currently investigating the situation and has no further comments at this time.
The probe was launched after a relatively new ransomware group named RansomedVC listed Sony on its Tor-based website, claiming to have compromised all Sony systems.
“We won’t ransom them,” the hackers said. “We will sell the data due to Sony not wanting to pay. Data is for sale.”
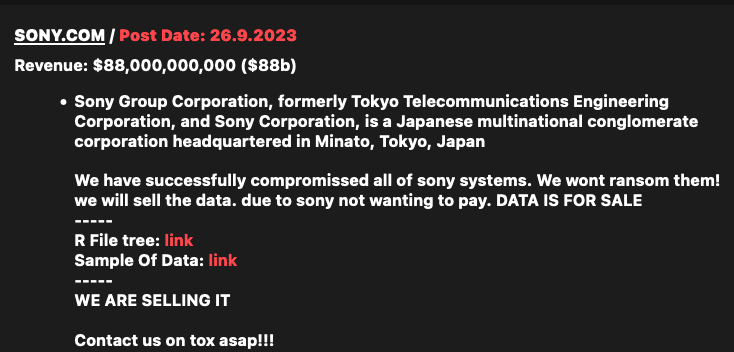
The cybercriminals have provided several files in an effort to demonstrate their claims, including some Java files and screenshots apparently showing access to source code and applications associated with Sony’s Creators Cloud media production solution.
One leaked file, a PowerPoint slideshow, is marked ‘confidential’ and appears to be from Sony’s quality department, but it’s dated 2017.
A majority of the leaked files seem to originate from servers associated with Creators Cloud and the hackers have not provided evidence that all Sony systems have been compromised. It’s not uncommon for these types of cybercrime groups to make exaggerated claims.
Threat intelligence group VX-Underground reported on X (formerly Twitter) that the cybercriminals did not deploy file-encypting ransomware or steal any corporate data. They allegedly exfiltrated data from Jenkins, SVN, SonarQube, and Creator Cloud development systems.
The RansomedVC group’s website currently lists nearly 40 victims, with ransom demands ranging between a few thousand dollars and $1 million, depending on the targeted organization’s size and revenue. The group announced its first victim in early 2023.
On the same day it announced Sony as a target, RansomedVC also listed Japanese mobile phone operator NTT Docomo as a victim on its website.
The gang claims they do not target Russian and Ukrainian organizations as most of its members are from these countries.
Cybersecurity firm Flashpoint described RansomedVC’s activities in August, pointing out its novel approach to extortion — using data protection laws such as the EU’s GDPR to justify attacks and pressure victims to pay up. Flashpoint at the time called for ‘cautious skepticism’ due to the group’s unverified claims.
Related: Sony Launches PlayStation Bug Bounty Program on HackerOne
Related: Sony Hackers Linked to Many Espionage, Destruction Campaigns
Related: N. Korea Calls Sony, Wannacry Hack Charges Smear Campaign
READ MORE HERE
