Someone Is Claiming To Sell A Mass Printer Hijacking Service
Internet-facing printers are exposed all over the world, leaving themselves open for hackers to print whatever they fancy. We saw hackers take advantage of unsecured printers last week, when someone bombarded offices and homes around the world with a printout urging them to subscribe to YouTuber PewDiePie.
Accessing printers en masse can still be somewhat technical though, so what if there was an easier way, that anyone could use? Now, someone is advertising printer hijacking as a service. Although it’s not clear whether the advert is more of a troll tactic and not a totally legitimate offer, the news still signals just how exposed many printers around the world are.
“Everyone will see your message,” an advert blasted out to internet-facing printers reads. On Sunday Andrew Morris, CEO of cybersecurity firm GreyNoise tweeted that the company had found someone sending print commands for this advert to the whole internet.
“Contact us […] to secure your spot in the most viral ad campaign in history,” the advert adds. Although we haven’t seen the advert successfully print, Morris tweeted out what it would have looked like based on the print commands GreyNoise found.
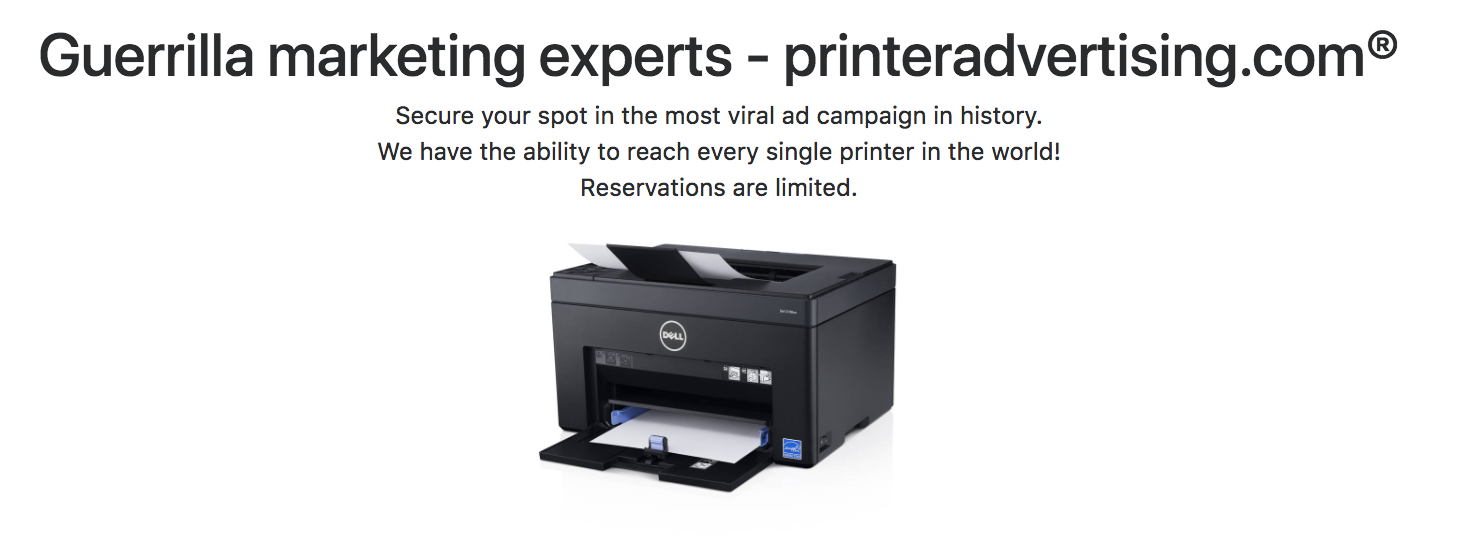
Caption: A screenshot of the mass printer hijacking service’s website. Image: Motherboard.
A Twitter account claiming to be linked to the campaign tweeted on Sunday “We’re currently mostly trying to see if anyone’s interested, if people actually want to buy this we’ll build a web platform with support for more printing protocols.”
The person in control of the operation’s email address told Motherboard that they’ve had lots of inquiries, but no sales just yet. They’re charging $250 for a single worldwide campaign, they added.
“Your message will reach vast amounts of printers all over the world at least once,” they wrote in an email.
Hackers have long toyed with printers connected to the wider internet. White supremacist Andrew “Weev” Auernheimer previously commanded a number of devices to print Nazi propaganda. In February last year, a hacker sent out commands to some 150,000 printers. And last week’s PewDiePie print-outs hit tens of thousands of printers, according to the hacker behind the campaign. Typically, a hacker may find vulnerable devices using the computer-search engine Shodan, and then write a script to target those particular printers. Shodan lets users search for printers with particular open ports or other characteristics.
Asked whether they would not print some types of material, such as Nazi propaganda, the person behind the operation said “I would certainly charge more to run such ads.”
Got a tip? You can contact Joseph Cox securely on Signal on +44 20 8133 5190, OTR chat on jfcox@jabber.ccc.de, or email joseph.cox@vice.com.
There is some reason to doubt the legitimacy of the service, though. On its website, the hackers say “We have the ability to reach every single printer in the world!” which is not possible because many printers not going to be accessible from the public internet.
At the bottom of the page, the website also links to the site and Instagram of Simon Smith, an Australian linked to the cybersecurity world. Smith denied having anything to do with the printing service.
“I most definitely (naturally) have nothing to do with the printer business. It is not only a negative SEO attempt, but a DDoS attempt on people’s fax machines and an attempt to deceive innocent victims as to the originating source,” he told Motherboard in an email on Monday.
The person behind the campaign added “In the past fax spam has been used to market various business services. I believe our advertising service would be especially interesting to companies offering printer paper/toner refills.”
Subscribe to our new cybersecurity podcast, CYBER.
READ MORE HERE


