Sextortion Botnet Spreads 30,000 Emails An Hour
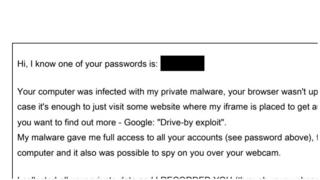 Image copyright Check Point
Image copyright Check Point A large-scale “sextortion” campaign is making use of a network of more than 450,000 hijacked computers to send aggressive emails, researchers have warned.
The emails threaten to release compromising photographs of the recipient unless $800 (£628) is paid in Bitcoin.
And they contain personal information – such as the recipient’s password – probably gathered from existing data breaches, to specifically target more than 27 million potential victims at a rate of 30,000 per hour.
While analysis suggests a small fraction of targets have fallen for the ploy, one expert said such botnets still offered a great “return on investment” for cyber-criminals.
“A botnet can be used for many, many things,” said Charles Henderson, from IBM’s X-Force Red security team. “This was just one task assigned to it.”
Hard to trace
A botnet is a network of computers taken over by hackers using malicious software typically spread via infected web pages or email attachments.
They can carry out attacks spread across a wide number of machines, making it harder to disrupt and the attacker’s origins harder to trace.
Security company Check Point said this latest sextortion attack used the Phorpiex botnet, active for more than a decade.
Research head Yaniv Balmas said those whose computers – Windows or Mac – had been hijacked would probably not know.
“Attackers are simply using the victims’ computers as vessels,” he said.
‘Save Yourself’
Spreading an email campaign across a botnet in this way would reduce the risk of the emails being flagged as spam – though it’s not clear how many were able to reach people’s inboxes.
“The criminals are getting smart enough to use a larger botnet and sending fewer emails per machine,” said Mr Henderson, who was not involved in Check Point’s research but has observed the same botnet in operation.
Experts advise using the latest versions of software – particularly web browsers, in this instance – to avoid being susceptible to this kind of attack.
A typical email sent by the botnet – with the subject line: “Save Yourself” – will say: “My malware gave me full access to all your accounts (see password above), full control over your computer and it was possible to spy on you over your webcam.”
The claim is not true but the emails include a genuine password associated with the target’s email address.
“The attacker is saying, ‘Hey, we hacked your computer, we saw you doing this and that, and this proves it. This is your password’,” Mr Balmas said.
‘Day jobs’
Check Point monitored one Bitcoin wallet used to collect funds from the scam and found about 11 bitcoin – almost $100,000 – was collected in a five-month period.
“Most people don’t fall for sextortion scams,” Mr Balmas said. “But it’s the rule of big numbers. If I’m sending 100,000 sextortion emails, it’s enough that 100 people fall for the trap. I get my money.”
He said it was likely the same botnet was being used to carry out other, more lucrative attacks, such as the theft of credit card details.
“It’s not somebody doing this from his garage,” Mr Balmas said.
“It’s a group of individuals doing this for their day jobs. This is their business.”
Follow Dave Lee on Twitter @DaveLeeBBC
Do you have more information about this or any other technology story? You can reach Dave directly and securely through encrypted messaging app Signal on: +1 (628) 400-7370.
READ MORE HERE
