Serious Apache Server Bug Gives Root To Baddies In Shared Environments

The Apache HTTP Server, the Internet’s most widely used Web server, just fixed a serious vulnerability that makes it possible for untrusted users or software to gain unfettered control of the machine the software runs on.
CVE-2019-0211, as the vulnerability is indexed, is a local privilege escalation, meaning it allows a person or software that already has limited access to the Web server to elevate privileges to root. From there, the attacker could do just about anything. The vulnerability makes it possible for unprivileged scripts to overwrite sensitive parts of a server’s memory, Charles Fol, the independent researcher who discovered the bug, wrote in a blog post. A malicious script could exploit the vulnerability to gain root.
The vulnerability poses the most risk inside Web-hosting facilities that offer shared instances, in which a single physical machine serves content for more than one website. Typically, such servers prevent an administrator of one site from accessing other sites or from accessing sensitive settings of the machine itself.
“If one of the users successfully exploits the vulnerability I reported, he/she will get full access to the server, just like the Web hoster,” Fol told Ars. “This implies read/write/delete any file/database of the other clients.”
The other likely scenario for exploit is in the event an attacker using a different attack gains only limited privileges on a server running Apache. If the server is vulnerable to CVE-2019-0211, the attacker could then exploit the flaw to elevate those limited privileges to root.
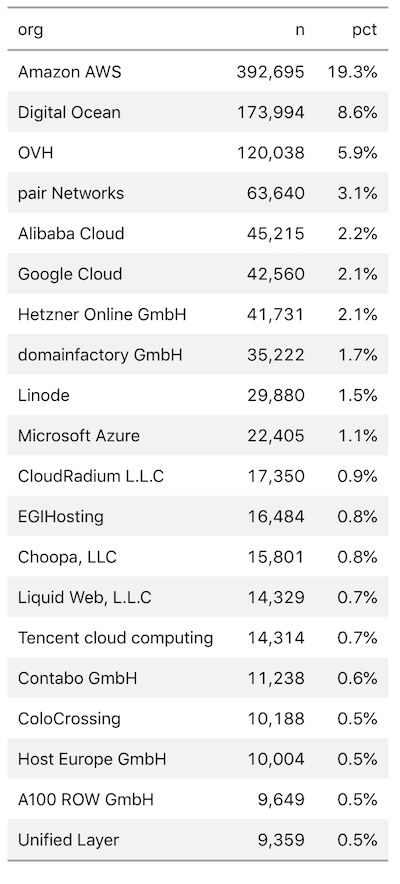
The vulnerability affects only Apache versions 2.4.17 to 2.4.38 when running on UNIX-like systems. According to security firm Rapid7, an estimated 2 million distinct systems were vulnerable to CVE-2019-0211, although most have likely updated since that number was published. Half of the vulnerable systems resided in what Rapid 7 called the “usual suspects,” or big cloud-hosting providers.
Here’s an image from the security firm of providers that were vulnerable at the time:
People who rely on Apache—particularly customers of hosts that provide shared instances—should ensure they’re running version 2.4.39.
READ MORE HERE