Revisiting 16shop Phishing Kit, Trend-Interpol Partnership

Analysis
Like other phishing kits, 16shop has a licensing mechanism that allows its subscribers to set up their own phishing panel and generate a lot of phishing sites and potential victims. It is a tool that lets cybercriminals setup phishing operations easily without needing to code from scratch. Cybercriminal subscribers only need to change the configuration file once they get the full package.
The panel has options for choosing the target brands, along with the prices. Scanning from the prices and payment methods’ options, the American Express (AMEX) scam page is the most expensive, likely due to the smaller number of “premium” credit card users.
The 16shop.co page can receive payment via a bank account based in Indonesia, or through a Bitcoin wallet. The cost ranges from US$60 to $70, except for the kit that targets AMEX users, which costs US$150. The Cash App mobile payment service, which was subsequently included among the targeted payment platforms in 2021, also costs $70. 16shop also provides a checker for stolen accounts in different companies such as Traveloka, Xiaomi, Etsy, Apple, and Malaysia Airlines.
In the phishing kits, we found some configurations like verify.ini in the preloaded messages in different languages, which indicates the targeted countries (aside from English-speaking countries) such as Japan, China, France, Spain, Malaysia, Germany, Thailand, and the Netherlands. The features of 16shop also provides the usual anti-phishing techniques such as anti-bot features like distinguishing security-related IP addresses, anti-sandbox, or geo-located restriction of access), get bank accounts (US only), and get Verified By Visa (VBV) or 3D Secure (3DS) of credit cards.
We tracked these phishing servers and found them mostly hosted by cloud service provider Digital Ocean. Cybercriminals use such services to ease out attack efforts and avoid the likelihood of detection by depending on a popular service providers’ addresses for deployment. For example, the IP server 128[.]199[.]154[.]155 contains a lot of ZIP files analyzed as phishing kits. We found more phishing sites with expired 16shop license keys, while a tweet in 2019 observed a phishing kit panel hosted in Unified Layer. In that Twitter post, the hosting server 68[.]183[.]236[.]100 was also reported to have a DigitalOcean ASN.
16shop operations and investigation
The business and construction operation of the phishing kit is nicely explained in a 2021 RSA talk (16shop as a case study is discussed at the 11:50 in the video). The lifecycle of operating a phishing campaign is divided into different phases, similar to the modus operandi of business email compromise (BEC) schemes such as Operation Killer Bee.
BEC operations fetch logs from notorious stealer malware, email extractors, or scrapers for potential target companies as the nature of BEC is focused on enterprises. Compared with phishing kit operators and sellers, the seller identifies personally identifiable information (PII) like email addresses to run a spam campaign on individuals or consumer-based sectors. Once the operator finds an effective phishing kit, the operator buys it and prepares for the kit’s infrastructure such as domains and servers. They also buy HTML and letter templates for the targeted brand/s and theme of the phishing scheme.
The operators deploy the kit to a virtual private server (VPS), installs the PHP into the web server, and copies the kit. This allows them to monitor the number of victims, locations, and general statistics of their campaign. Next, they build the payload for the mass mailing of phishing emails, along with the letter template, HTML pages, and even shortlink-based sites for SMS. In cases like malware stealer AgentTesla, the operators use an automated email-sending software like Gammadayne and purchase an SMTP server, or sometimes abuse a stolen SMTP server, and run the spam campaign.
When the phishing campaign is initiated, victims are redirected to spoofed pages, which uses fake forms to lure them into providing their PII. The last phase of the operation involves collecting the stolen PII in the form of email, log files, or even from chat apps like Telegram via API. The cybercriminals will be able to use the stolen PII, especially credit card information, or sell this to carding shops to earn profit.
All the processes require payment in the form of cryptocurrencies or, sometimes, cash. The overall ecosystem of a phishing campaign is made up of and dependent on:
- The operator that buys phishing kits and infrastructure
- The developer and builder of the phishing source code
- The infrastructure broker that advertises the VPS, email and hardware for operators
- The illicit market that advertises buying and selling of their services
Domains’ timeline
The domains were created in the following years:
- 2017: 16digit.shop
RNS says in an interview that 16shop phishing kit was started and developed with a colleague.
- 2018: 16shop.online
In 2018, 16digit.shop was replaced by 16shop.online, which may indicate that it is operated by the main admin owner. Although there is no registrant email address and name, the registrant’s location was identified to be in Indonesia.
- 2019: 16shop.us
The domain 16shop[.]us became active in 2019 and was hosted on server 89[.]203[.]249[.]185. This is the same host server with 16digit[.]shop, the first domain of the administrator’s initials “RNS.” Interestingly, a phishing domain, appleidnotice[.]apphelpa[.]cc, was resolved to this IP address in 2017, which might indicate the early phishing development of the admin RNS.
- 2020: 16shop.co
The 16shop.co domain was hosted on the same server of 16shop.us, which is 68[.]183[.]178[.]69 and identified to be hosted by Digital Ocean. The certificate domain of 16shop.us was 16shop.co, which indicates that it was being used by the same admin panel owner. The 16shop.co domain resolved to another IP address: 128[.]199[.]252[.]82, registered to Digital Ocean. Pivoting from this IP address led to two more 16shop domains: 16shop.vip, which is the reported domain for Cash App as another target brand. The other domain is an unusually formatted domain: 16shop.lx-coding.in.
- 2021: 16shop.vip
The domain 16shop.vip was used as a subject alternative name in the SSL certificate of 16shop.lx-coding.in. Following the domain lx-coding.in led us to a GitHub account with the handle “lxcoding666” pinned. This then led to another threat actor with the initials “L J,” where we found an Instagram account (previously having same profile photo with the GitHub account but was recently changed to a photographer’s profile. A report featuring “RNS” said he no longer develops 16shop and instead focused on photography). “L J” speaks Indonesian and has several underground accounts, including a blog about being a Java bounty hunter, participation in a credit card hacking forum, and a discussion on topics like stolen PayPal accounts.
Other domains, like 16shop.club and 16shop.online that considered the early versions of the 16shop admin panel, were seen active in 2019. The domains 16digit.shop and 16shop.us were registered by root.devilscream@gmail[.]com with the registrant’s full name mentioned in the RIF Name Service (RNS). Security analysts initially dubbed the threat actor as “DevilScream,” who was found to have a history of writing exploit codes and defacing several websites.
The investigation on the main developer or admin of 16shop was identified because of the threat actor’s poor operational security. In 2021, he contacted Cyberthreat.id and initiated an interview to address his involvement with the report of 16shop that targeted Cash App. He mentioned in the interview that since 2019, that he was no longer involved in developing the phishing kit. However, the 16shop.vip domain that hosted the additional target brand Cash App was active around April 2021. This domain appeared active as a 16shop admin panel and was registered in 2021 with an alternative registrant email address, phone number, and name. Using the Open Source Intelligence (OSINT) tool Social Links, the phone was connected to another email address, and we found that both emails were registered in an e-commerce company based in Indonesia in 2018 and 2019. Both emails also under the name of “RNS,” and one of the emails — along with the phone number — is available for reference with Indonesian Court records.
Aside from 16shop, we also investigated phishing kits tracked to be based in Indonesia, and some are listed in the table below, as reported by security researcher JcyberSec_. In 2021, we also investigated the possible actor and phishing server of an Office365 scam page kit, a phishing campaign that targeted high ranking company executives since 2019 and reused the compromised accounts to target more. We included these kits to highlight how 16shop was widely used and reused, becoming the most used phishing kit among cybercriminals, and most analyzed among security researchers.
Cooperation with Interpol
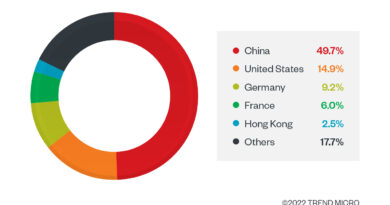
Local law enforcement agencies in Japan and Indonesia have conducted their respective interviews and investigations on the arrested facilitators of 16shop on how they profited in millions from the stolen credit card information. Due to the financial impact of 16shop to the financial sector and consumers, Interpol spearheaded an investigation. In 2020, we received a request for information and have been actively investigating these phishing campaigns since with the agency, gathering intelligence on the threat actors involved. We gauged the impact of this phishing campaign heavily targeting and affecting Japan, the US, and Germany. In 2022, Indonesian police apprehended the phishing kit developer in coordination with Interpol and FBI. The aim was to apprehend the main administrator of the phishing kit and to take down the main phishing servers so 16shop’s services and stop purchase transactions from its customers.
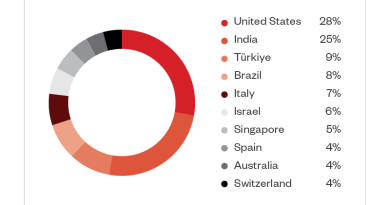
According to the Attorney’s General Office case file, the suspect was identified to develop and sell source code or scripts of 16shop phishing-as-a-service, which could hack international electronic payment accounts and credit cards. The source code features anti-bot and anti-phishing detection capabilities, supports eight languages, and would automatically load to the victim’s device depending on the geolocation. This phishing campaign aimed to fetch sensitive or personal data from account owners such as credit card numbers, usernames, passwords, ID cards, telephone numbers, and other supporting data. The perpetrator also targeted more than 70,000 accounts of multiple international companies across 43 countries, and the amount of loss is estimated to be around Rp. 127 billion (US$8 million).
Whilst 16shop was still operating after the main administrator was apprehended, we observed that the admin panel 16shop[.]vip with registrant details still links to “RNS,” a.k.a. DevilScream. 16shop is currently no longer active, and local police in Indonesia and Japan conducted two more follow-up arrests from this operation with aid from Interpol.
This outstanding partnership of Trend Micro with Interpol continues as we carry on our mission to provide a safer world in cyberspace. We were given the opportunity to help enhance the intelligence and shared information through requests and exchanging information, resulting in a collaborative and coordinated action from law enforcement agencies from different countries.
Read More HERE