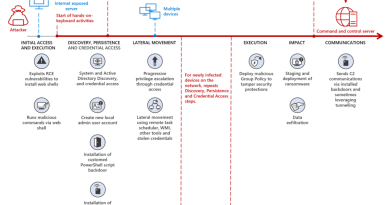
Rethinking cyber scenarios—learning (and training) as you defend
In two recent posts I discussed with Circadence the increasing importance of gamification for cybersecurity learning and how to get started as a practitioner while being supported by an enterprise learning officer or security team lead. In this third and final post in the series, Keenan and I address more advanced SecOps scenarios that an experienced practitioner would be concerned with understanding. We even show how Circadence and Microsoft help seasoned practitioners defend against some of the most prevalent and advanced attackers we see across industries.
Here are more of Keenan’s insights from our Q&A:
Q: Keenan, thanks for sharing in this digital conversation with me again. I admire your passion for gamified cyber learning. I’d not put the two ideas together, that you can adopt gaming concepts—and consoles—in a way that makes learning the often difficult and evolving subject matter of “cyber” much more fun and impactful. Now that I’ve used Project Ares for a year, it’s hard to imagine NOT having an interactive, gamified platform to help me build and refine cybersecurity concepts and skills. Several friends and colleagues have also registered their teenagers for Circadence’s Project Ares Academy subscriptions to kickstart their learning journey toward a cyber career path. If kids are going to game, let’s point them to something that will build employable skills for the future.
In our last two blogs, we introduced readers to a couple of new ideas:
Now, let’s pivot and focus on practical cyber scenarios (let’s say Tier 1 or Tier 2 defender scenarios)—situations that would likely be directed to experienced cyber professionals to handle. Walk us through some of detail about how Circadence has built SecOps gaming experiences into Project Ares through mission scenarios that are inspired by real cyber incidents pulled from news headlines incorporating today’s most common attack methods such as ransomware, credential theft, and even nation-state attacks?
A: Sure. I’ll start with descriptions of a couple of our foundational missions.
Scenario one: Ransomware—Project Ares offers several mission scenarios that address the cyber kill chain around ransomware. The one I’ll focus on is Mission 10, Operation Crimson Wolf. Acting as a cyber force member working for a transportation company, the user must secure networks so the company can conduct effective port activity. However, the company is in danger as ransomware has encrypted data and a hacker has launched a phishing attack on the network, impacting how and when operators offload ships. The player must stop the ransomware from spreading and attacking other nodes on the network before it’s too late. I love this scenario because 1) it’s realistic, 2) ransomware attacks occur far too often, and 3) it allows the player to engage in a virtual environment to build skills.
Users who engage in this mission learn core competencies like:
- Computer network defense.
- Incident response management.
- Data forensics and handling.
We map all our missions to the NIST/NICE work role framework and Mission 10 touches on the following work roles: System Security Analyst, Cyber Defense Analyst, Cyber Defense Incident Responder, and the Cyber Defense Forensics Analyst.

Scenario two: Credential theft—Another mission that’s really engaging is Mission 1, Operation Goatherd. It teaches how credential theft can occur via a brute force attack. In this mission, the user must access the command and control server of a group of hackers to disable a botnet network in use. The botnet is designed to execute a widespread financial scam triggering the collapse of a national bank! The user must scan the command and control server located at myloot.com for running services, identify a vulnerable service, perform a brute force attack to obtain credentials, and then kill the web server acting as the command and control orchestrator.
This scenario is powerful because it asks the player to address the challenge by thinking from an adversary’s perspective. It helps the learner understand how an attacker would execute credential theft (though there are many ways) and gives the learner a different perspective for a well-rounded comprehension of the attack method.
Users who engage in this mission learn core competencies like:
- Network protocols.
- Reconnaissance and enumeration.
- Password cracking and exploration.
The NIST/NICE work role aligned to this mission is a Cyber Operator. Specific tasks this work role must address include:
- Analyzing target operational architecture for ways to gain access.
- Conducting network scouting and vulnerability analysis of systems within a network.
- Detecting exploits against targeted networks.

Q: Can you discuss how Project Ares’ learning curriculum addresses critical threats from advanced state or state-backed attackers. While we won’t name governments directly, the point for our readers to understand is that the national and international cybersecurity stage is built around identifying and learning how to combat the tools, tactics, and procedures that threat actors are using in all industries.
A: Here’s a good example.
Scenario three: Election security—In this mission, we deploy in our next release of Project Ares, which now leverages cloud native architecture (running on Microsoft Azure), is Mission 15, Operation Raging Mammoth. It helps a cyber professional protect against an election attack—something we are all too familiar with through recent headlines about election security. As an election security official, the user must monitor voting systems to establish a baseline of normal activity and configurations from which we identify anomalies. The user must detect and report changes to an administrator’s access permissions and/or modifications to voter information.
The NIST/NICE work roles aligned to this mission include professionals training as a Cyber Defense Analyst, Cyber Defense Incident Responder, or Threat/Warning Analyst.

I’ve reviewed some of the specific cyber scenarios a Tier 1 or Tier 2 defender might experience on the job. Now I’d like to share a bit how we build these exercises for our customers.
It really comes down to the professional experiences and detailed research from our Mission and Battle Room design teams at Circadence. Many of them have explicit and long-standing professional experience as on-the-job cyber operators and defenders, as well as cyber professors and teachers at renowned institutions. They really understand what professionals need to learn, how they need to learn, and the most effective ways to learn.
We profile Circadence professionals in the Living Our Mission Blog Series to help interested readers understand the skill and dedication of the people behind Project Ares. By sharing the individual faces behind the solution, we hope current and prospective customers will appreciate Project Ares more knowing that Circadence is building the most relevant learning experiences available to support immersive, gamified learning of today’s cyber professionals.
Learn more
To see Project Ares “in action” visit Circadence and request a demonstration, or speak with your local Microsoft representative. You can also try your hand at it by attending an upcoming Microsoft Ignite: The Tour event, which features a joint Microsoft/Circadence “Into the Breach” capture the flag exercise.
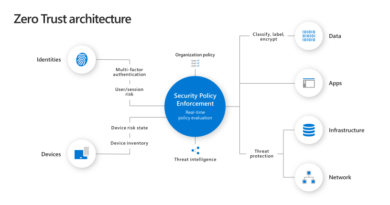
To learn more about how to close the cybersecurity talent gap, read the e-book: CISO essentials: How to optimize recruiting while strengthening cybersecurity. For more information on Microsoft intelligence security solutions, including guidance on Zero Trust, visit Reach the optimal state in your Zero Trust journey.
READ MORE HERE