Researchers reckon 500k PCs infested with malware after dodgy downloads install even more nasties from Bitbucket
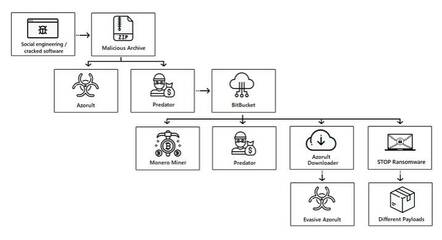
We don’t know who needs to hear this, but don’t download cracked commercial software. Researchers claim more than 500,000 PCs have been left wriggling with malware after a cracked app went on to retrieve further nasties from Bitbucket repos.
Security company Cybereason has studied a campaign to deliver “an arsenal of malware” including credential stealers, cryptocurrency miners, ransomware and crypto-coin pinchers.
“It is also able to take pictures using the camera [and] take screenshots,” wrote researchers Lior Rochberger and Assaf Dahan.
How this stuff was managed and coordinated without bringing the user’s machine to a standstill is not specifically mentioned, but the duo added that “the combination of so many different types of malware exfiltrating so many different types of data can leave organisations unworkable”.
Users generally start their journey to hell, according to the paper, by “downloading a cracked version of commercial software like Adobe Photoshop, Microsoft Office, and others”. There is an insatiable appetite for free versions of expensive software, it seems, and search engines are happy to help. We searched Bing for “Download Adobe” and right at the top of the page were videos with guides to illegal downloads; no, we did not test these for malware but it would not be surprising if they came with some unwanted extras.
Rochberger and Dahan reckon that some such downloads create a connection to Bitbucket repositories to install “additional payloads”. Bitbucket is a code-management platform from Atlassian. There is no suggestion that Bitbucket itself has any specific vulnerabilities, but the claim is that serving malware from legitimate sites such as this – or others like Github, Dropbox and Google Drive – makes it harder for security software to detect. In addition, the researchers said the repositories are “updated almost constantly by the threat actor” in order to evade antivirus signature lists.
As is common, there is a marketing element to the report, with the researchers recommending an “iterative security process” to defend against this kind of attack.
Despite the researchers’ “Hole in the bucket” headline, the real story here is the risks inherent in users trying to get commercial software for free. Atlassian was quick to remove the malicious repositories reported to them, but the scale of services like this is such that preventing further occurrences is likely to be unrealistic. ®
Sponsored: Detecting cyber attacks as a small to medium business
READ MORE HERE